Eliminate hard-coded and long-lived credentials – and build truly resilient software deployment pipelines – with a unified identity system across clouds.
Glad you listened, and even happier you’re here!
In the episode, Aembit Co-Founder & CEO David Goldschlag walked the guys through the real problem with agent-to-service connections today: Software is reaching across more boundaries than ever, and too many agents still borrow human credentials or rely on long-lived secrets. The result is lost attribution, weaker controls, and access patterns that do not scale.
• Agents now move across more tools and services than identity models were built for.
• Inherited human credentials remove the guardrails that keep agent access in check.
• Shared identities make it unclear whether the agent or the person acted.
• Long-lived secrets give agents more reach than intended.
• Access time identity checks keep agent behavior clear and auditable.
AI isn’t a human and its access can’t be effectively managed the same way. With Aembit, you get continous identity verification, run-time policy enforcement, and context-based access controls for apps, services, and AI agents. Get a centralized control point for all of it.

“Agentic AI was driving our search for a secure way to control non-human access. Aembit is a step ahead – they solved this elegantly at enterprise-scale.”

“Aembit is a game changer! Along with making us more secure, Aembit also helps automate existing processes. We estimate that Aembit can save us five to 10 hours a day.”

“Securing workload identities is the foundation of a secure by default approach to security. Aembit provides an elegant approach that works across clouds, containers, APIs and SaaS services.”

“Identity is the cornerstone of zero trust. Today robust workload IAM is out of reach of all but the most sophisticated organizations. Aembit is democratizing workload IAM for all enterprises.”
FEATURES
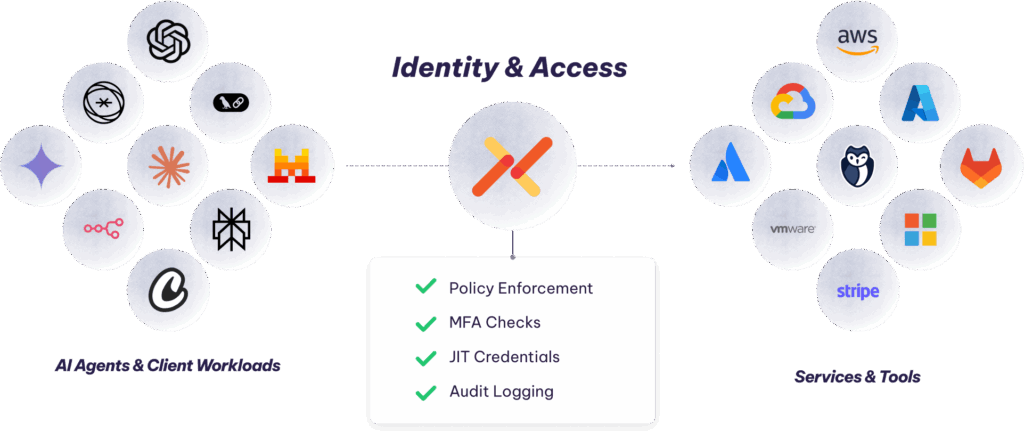
Aembit is an independent identity broker that can secure access for AI agents, MCP servers, and workloads among clouds, SaaS, and on-premise data centers. It’s one central place to enforce & audit access from agents to sensitive resources.
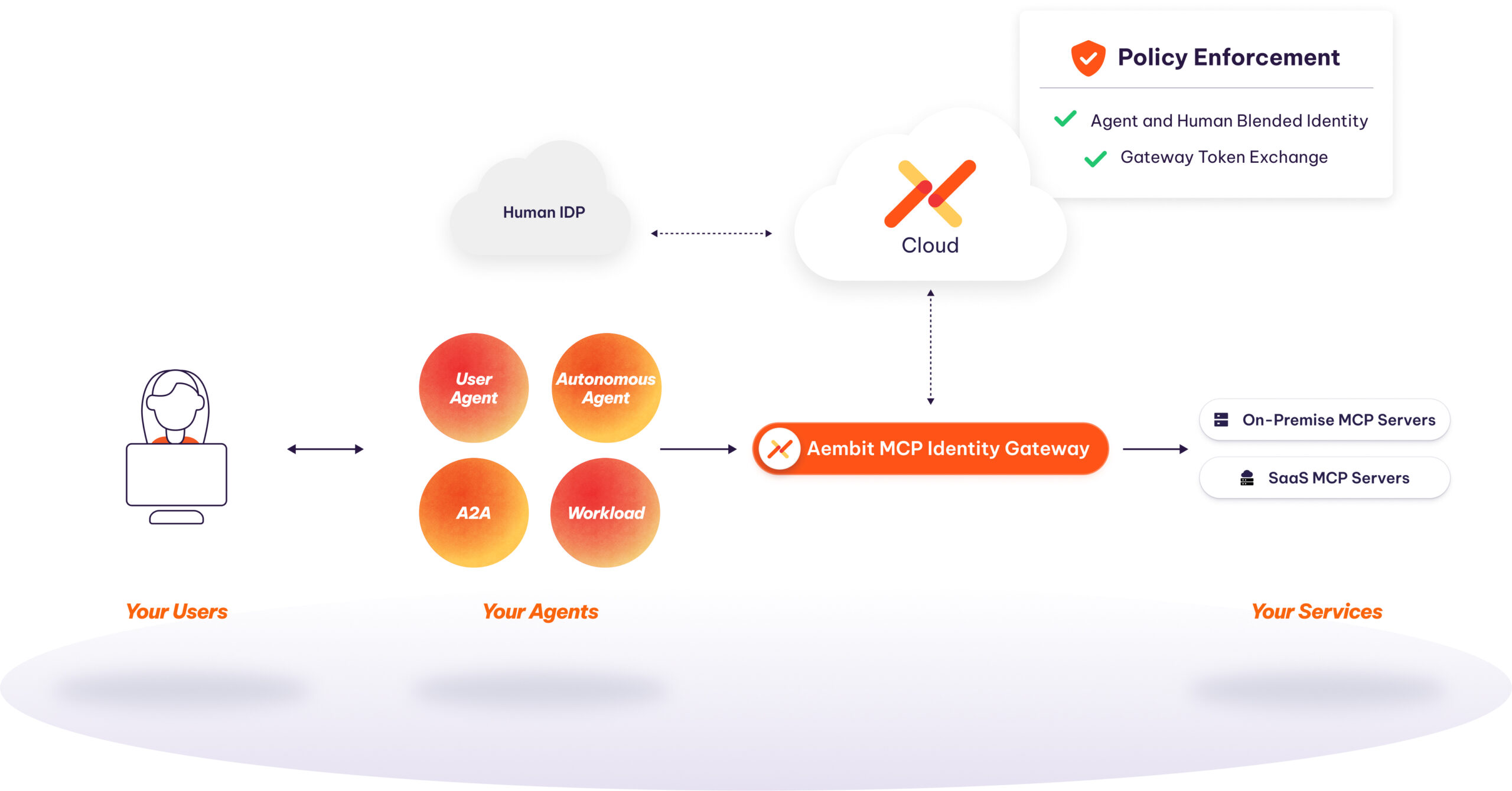
Manage agentic AI access to MCP through a single, auditable data plane. Combine Agent+User into a Blended Identity , combined with the real-time policy enforcement, token exchange, and credential isolation of the Gateway.
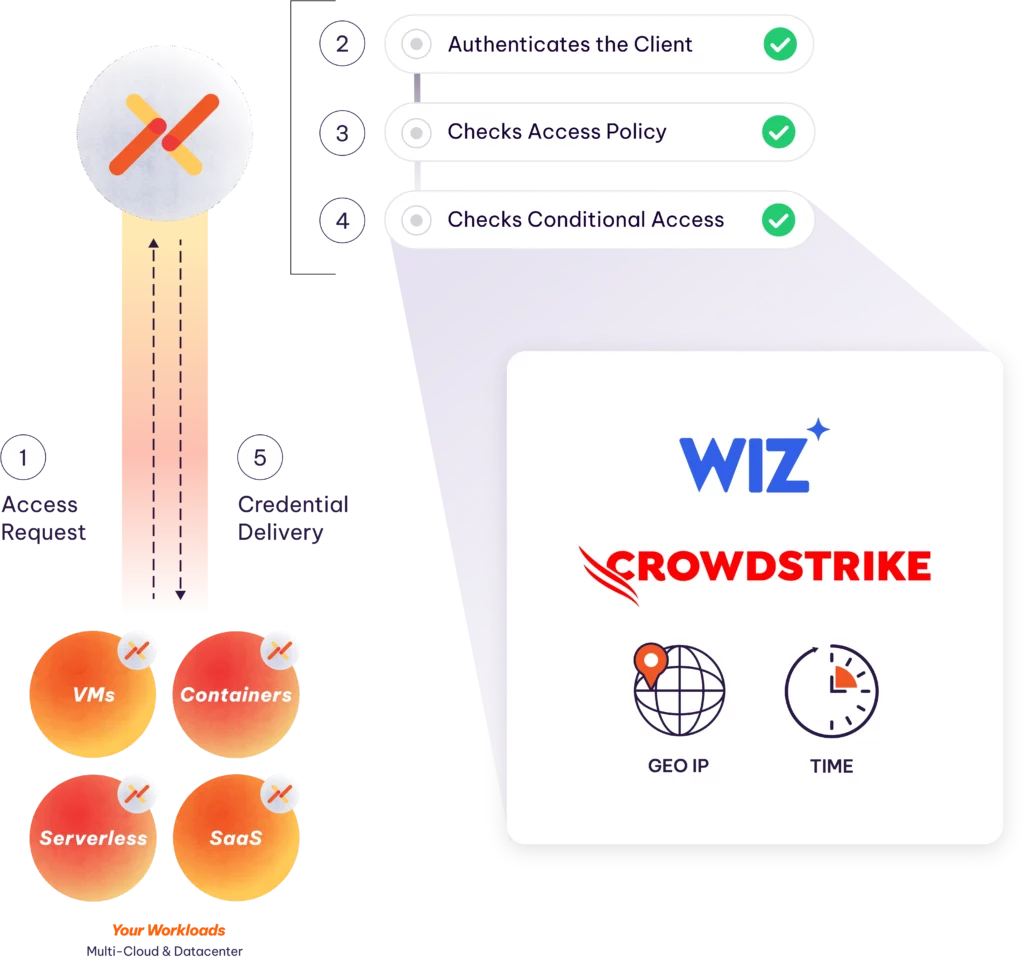
Don’t allow agents or workloads to store or share secrets. Instead, use Aembit to deliver a secret just-in-time, per task, and without developer overhead.
Dynamically enforce access rights based on real-time evaluations of AI Agent security posture, geography, time windows and other key behaviors.
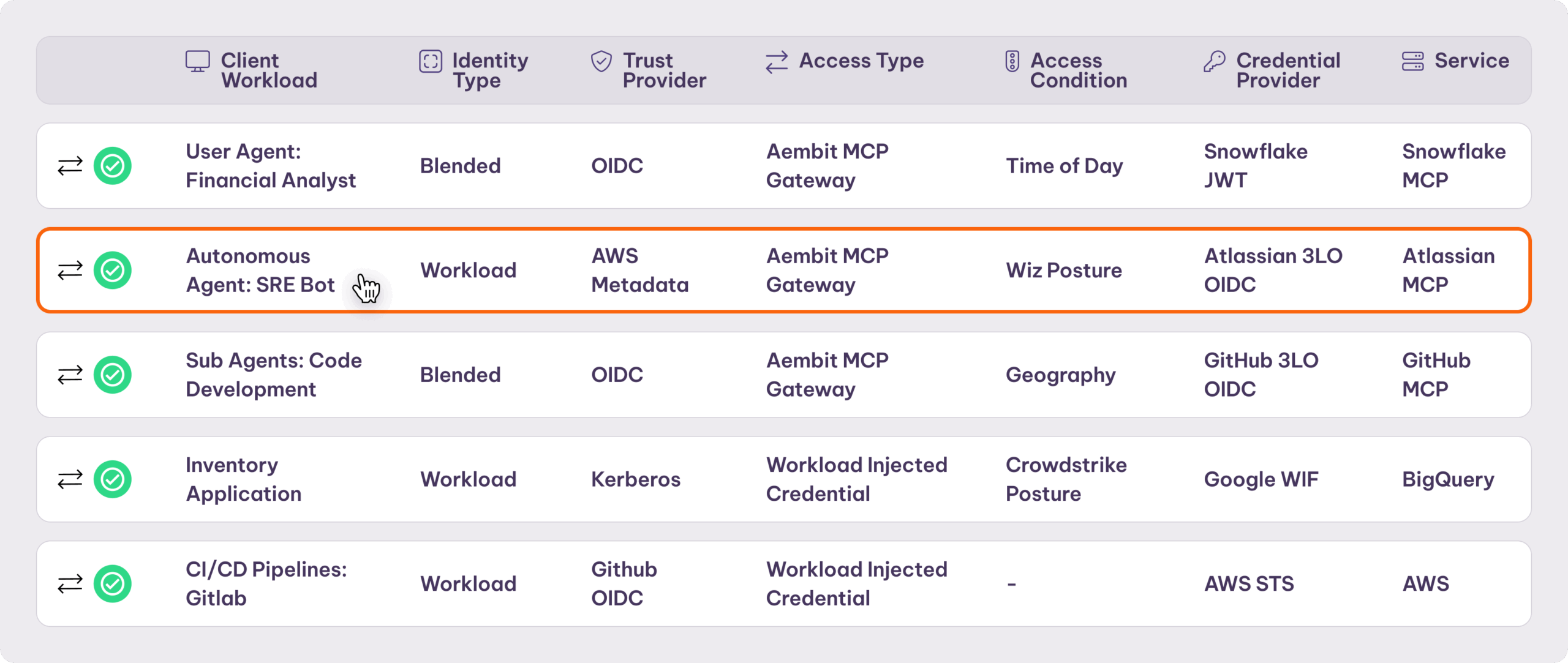
See exactly what AI agents and workloads access – not hidden behind users or their parent agents. See everything based on each agent’s unique identity.
Streamline and secure access from AI agents to leading LLMs like OpenAI, Claude, and Gemini, APIs, and tools with policy-based, identity-driven controls.
The explosion of Agentic AI is posing new challenges for security and DevOps teams across all industries and organizational sizes.
Eliminate hard-coded and long-lived credentials – and build truly resilient software deployment pipelines – with a unified identity system across clouds.
Get started in minutes, with no sales calls required. Our free- forever tier is just a click away.