Create and enforce policies that define NHI access from applications, scripts, serverless functions, and more.
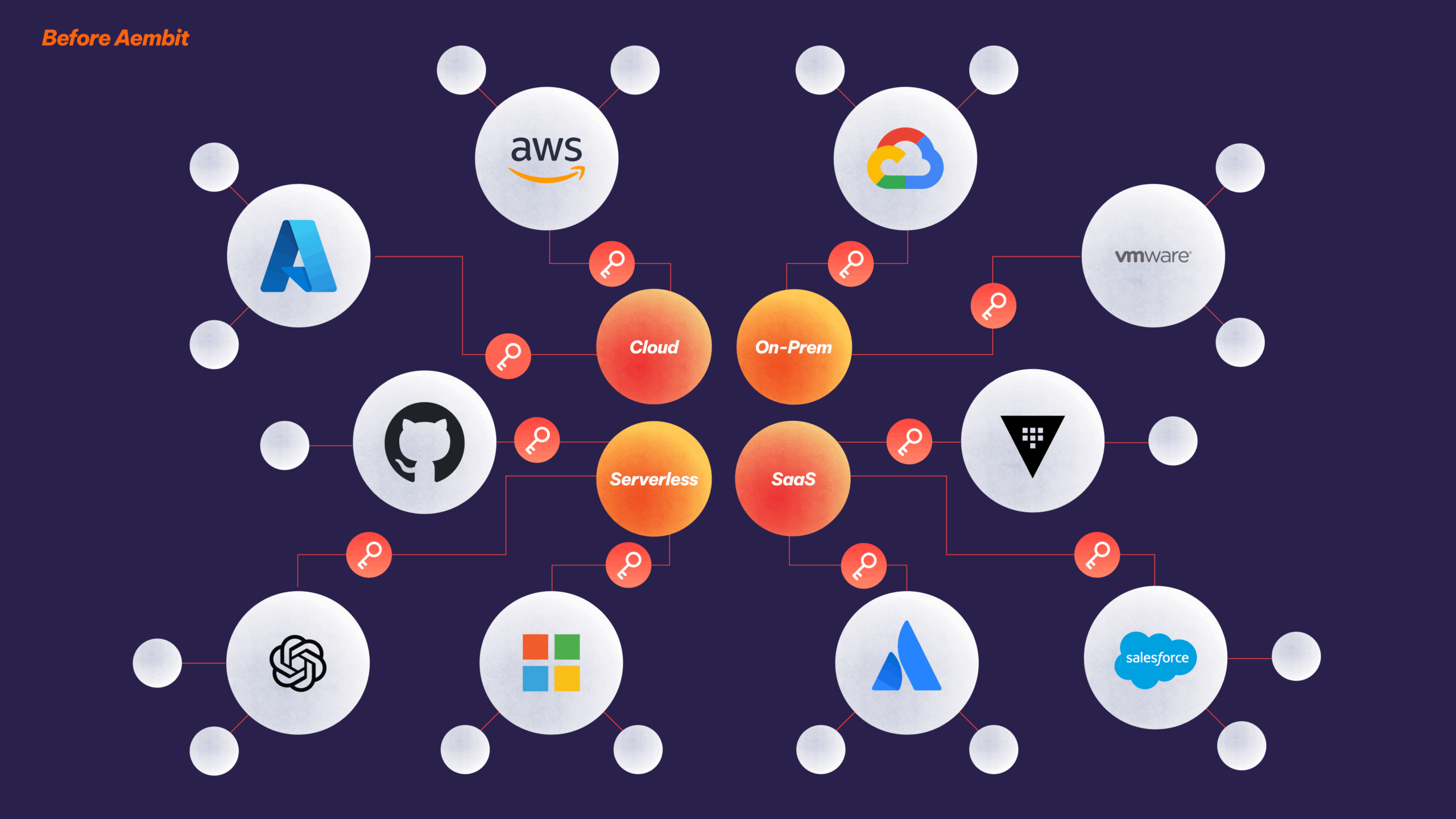
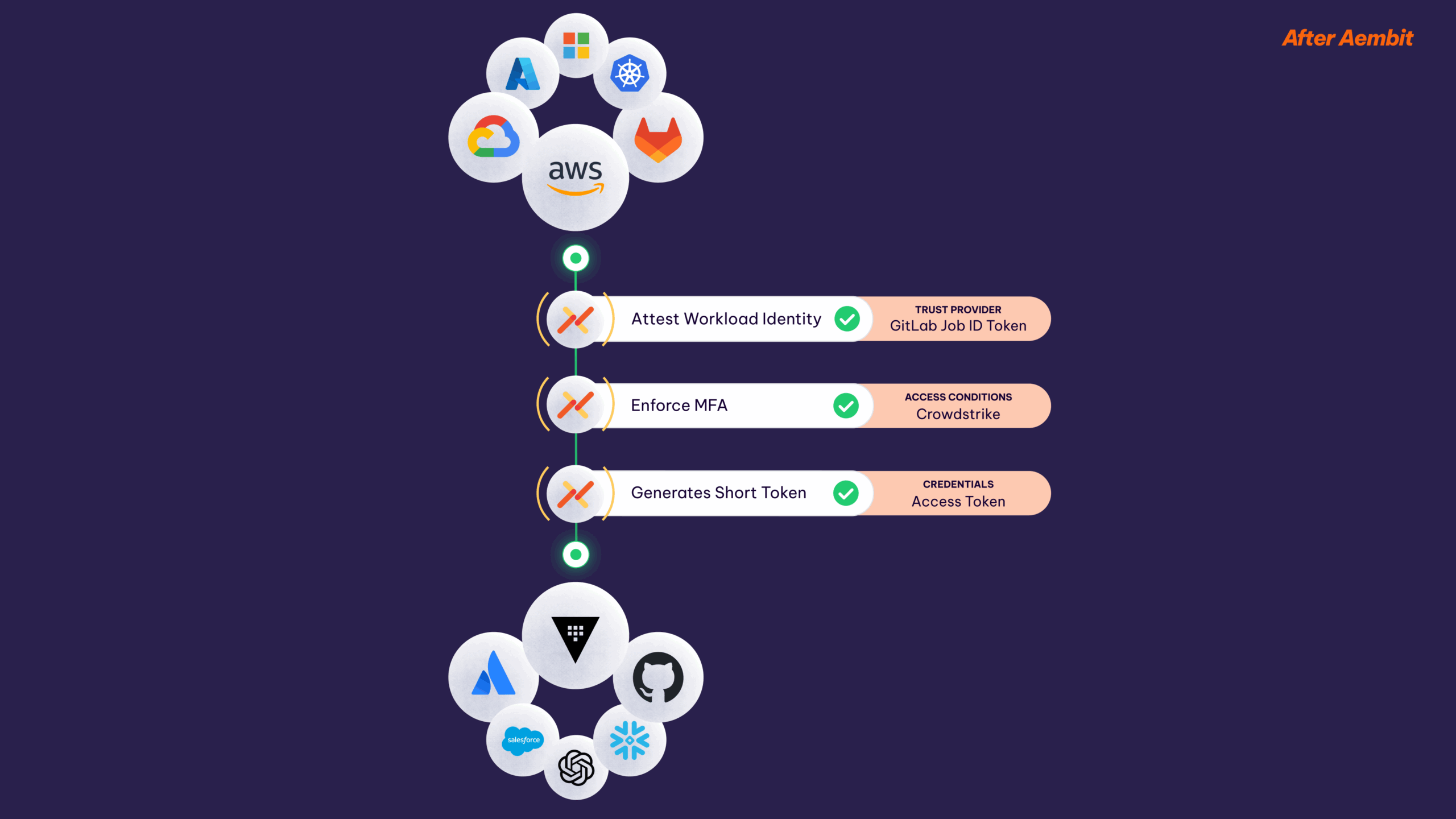
Only Aembit brings together the right mix of capabilities to move your IAM strategy forward in both your production and corporate IT environments.
A global policy system that allows you to define and enforce access policies between NHIs in and across multiple environments.
Go beyond identity. Use dynamic, configurable factors such as risk posture, time, and geo to determine whether or not access is granted to a workload.
Aembit uses client environment attestation for Secretless Workload Authentication. The client no longer needs a long-lived identity secret – one less thing to manage or lose.
Aembit logs access attempts in a single format, giving you pre-packaged queries to simplify audit, logging, and incident response. Easily view logs in Aembit or your SIEM.
A single uniform way to work across clouds, on-premise data center, SaaS services, and third-party APIs by creating credential providers for multiple services and environments.
Aembit removes the burden of coding auth, while ensuring that Identity and Access Management is implemented effectively everywhere. It works for existing workloads with no code changes.
Gain control with a unified, policy-based approach to non-human IAM that works for modern applications, legacy apps, and across clouds and on-premises. Manages access at scale, where you need it.
DevOps and Security have a single place to enforce, manage, and log access, with no developer burden through no-code auth.
A single IAM platform so your workloads can interact across data centers, clouds, SaaS services, and third-party APIs.
“Identity is the cornerstone of Zero Trust. Today robust workload IAM is out of reach of all but the most sophisticated organizations. Aembit is democratizing workload IAM for all enterprises.”

“Aembit is a game changer! Along with making us more secure, Aembit also helps automate existing processes. We estimate that Aembit can save us 5-10 hours a day.”

“Securing workload identities is the foundation of a secure by default approach to security. Aembit provides an elegant approach that works across clouds, containers, APIs and SaaS services.”
Wherever you build, Aembit will be there to support you. Your client workloads can live in a range of different environments that we support out of the box.









Workload authentication uses a range of approaches, and our goal is to help you uniformly support them all.
Wherever you’re connecting, we’ll make it easy for you with our out-of-the-box integrations with the most popular APIs and Services. This list is always growing, and we work with you as you need specific workloads.












Grant access based on additional, dynamic and configurable characteristics of workloads such as security posture, time of day, workload geography and more.
Get started in minutes, with no sales calls required. Our free- forever tier is just a click away.