Create and enforce policies that define when AI agents and workloads can access sensitive resources.
Eliminate the need to manage or store credentials.
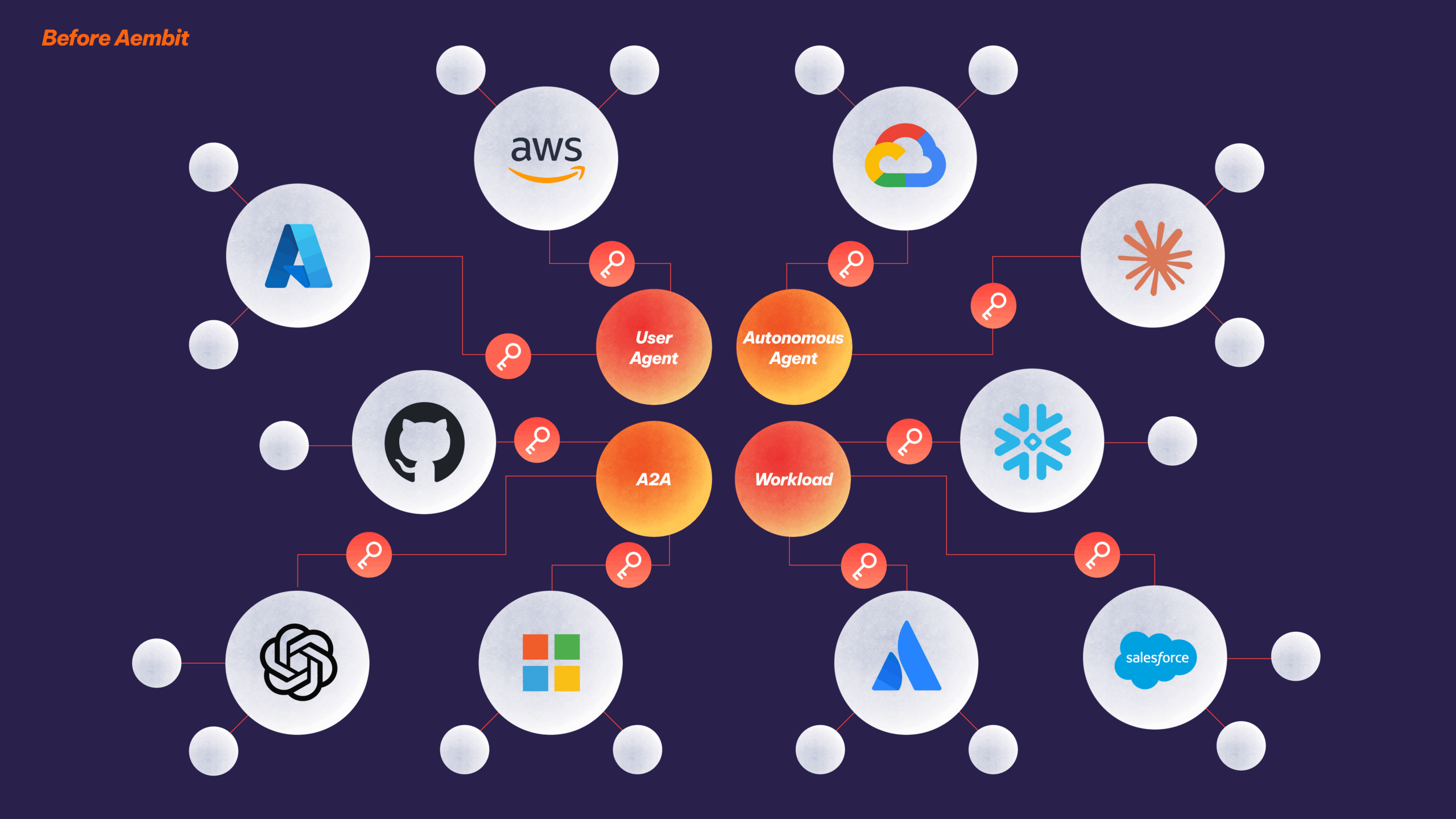
Only Aembit brings together the right mix of capabilities to move your IAM strategy forward in both your production and corporate IT environments.
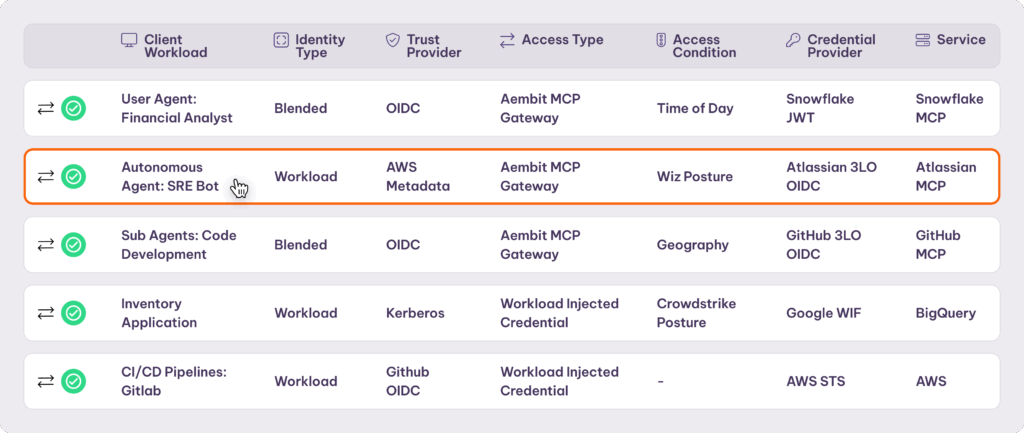
A global policy system that allows you to define and enforce access policies between NHIs in and across multiple environments.
Apply a cryptographically verifiable, secretless identity to every agent. Then, blend in upstream context from the user operating the agent. Define access based on this unique identity.
Go beyond identity. Use dynamic, configurable factors such as risk posture, time, and geo to determine whether or not access is granted to a workload.
Aembit logs access attempts in a single format, giving you simplified access audit, logging, and incident response. Every log contains attribution so you know if it was from an agent, a workload or a user-driven agent. View logs in Aembit or your SIEM.
A single uniform way to work across clouds, on-premise data center, SaaS services, and third-party APIs by creating credential providers for multiple services and environments.
Aembit removes the burden of coding auth, while ensuring that Identity and Access Management is implemented effectively everywhere. It works for existing workloads with no code changes.
.
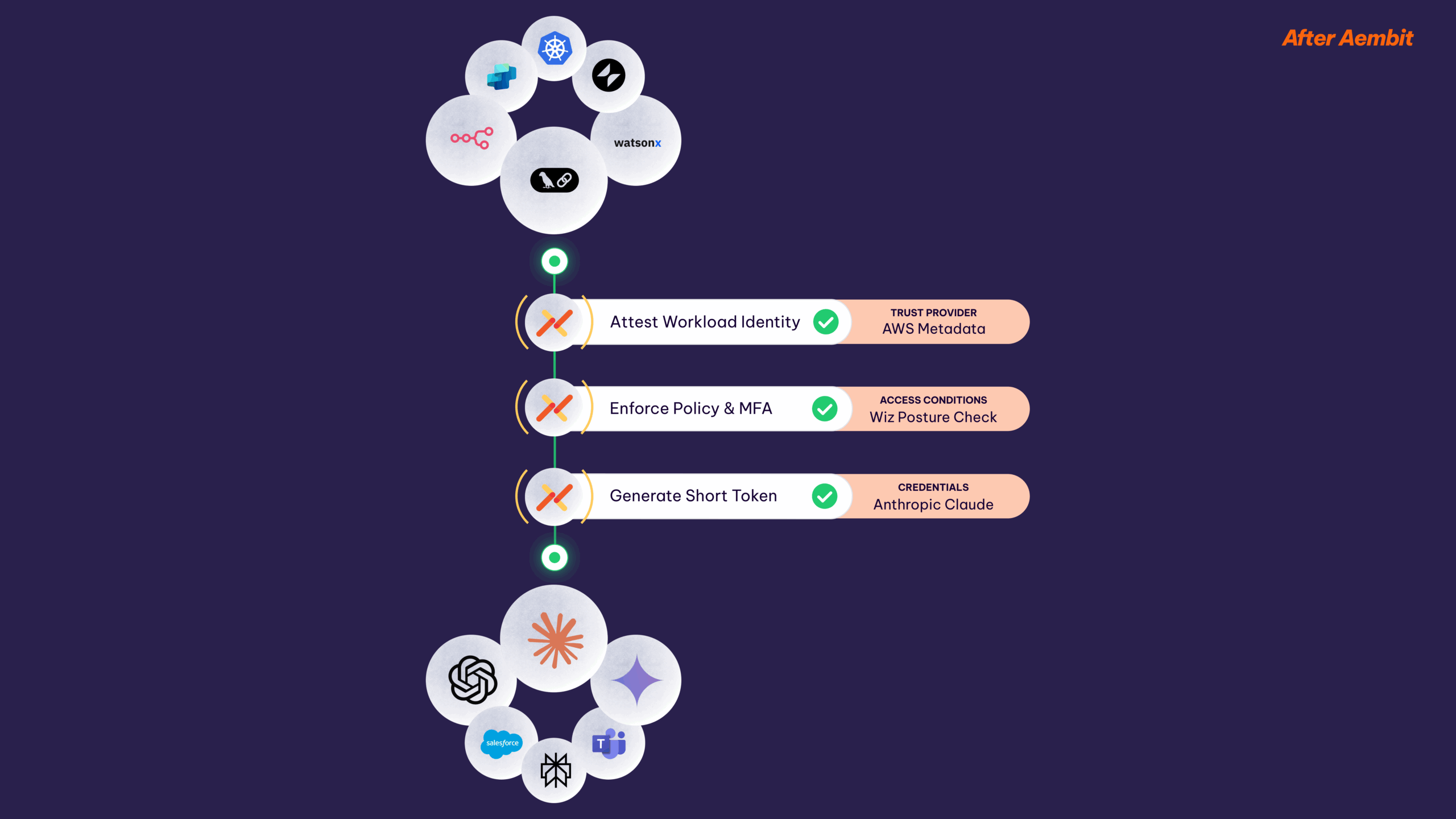
Simply define an agent or workload, what it can access, and the identity verification method. Then define conditional access – like MFA, for machines.
Then Aembit will provide runtime verification, policy enforcement, and deliver short-lived credentials at every access attempt.
Gain control with a unified, policy-based approach to non-human IAM that works for modern applications, legacy apps, and across clouds and on-premises. Manages access at scale, where you need it.
DevOps and Security have a single place to enforce, manage, and log access, with no developer burden through no-code auth.
A single IAM platform so your workloads can interact across data centers, clouds, SaaS services, and third-party APIs.
Stop wondering what AI Agents are accessing your data, or where secrets are being managed. Instead, implement the capability to proactively enforce in real-time when workloads can touch sensitive resources.
AI Agents:
Use Aembit to provide AI agents just-in-time access based on their deployment model, use case, and the human interacting with the agent. Eliminate the need to store & manage credentials or code auth.
Traditional Workloads:
Use Aembit to provide a range of traditional workloads like scripts, apps, and pipelines with secretless, just-in-time access based on policies you control. No more secrets management or brittle auth code.
Developer Laptops:
Aembit can provide access to dev/test code on a developers' laptop, similar to that of traditional workloads. Take advantage of the developer identity in addition to policies for the workload.
Aembit MCP Identity Gateway:
Aembit's MCP Identity Gateway is a control point that exchanges an AI agent's access token for the appropriate MCP server credentials, without exposing those credentials to the agent.
Batch Jobs:
Batch jobs may directly access your sensitive data and systems, or may be triggered by AI agents or other workloads. Aembit both enforces access to batch jobs from other workloads, and from batch jobs to other resources. With Aembit, these workloads never need to directly store or provide sensitive access credentials.
Legacy Apps:
Legacy apps may directly access your sensitive data and systems, or may be triggered by AI agents or other workloads. Aembit both enforces access to legacy apps from other workloads, and from legacy apps to other resources. With Aembit, these workloads never need to directly store or provide sensitive access credentials.
Microservices:
Microservices may directly access your sensitive data and systems, or may be triggered by AI agents or other workloads. Aembit both enforces access to microservices from other workloads, and from microservices to other resources. With Aembit, these workloads never need to directly store or provide sensitive access credentials.
API Gateways:
API gateways are strategically placed between AI agents or other workloads and your resources. Aembit both enforces access to API gateways from other workloads, and from API gateways to other resources. With Aembit, these workloads never need to directly store or provide sensitive access credentials.
Cloud:
Aembit Cloud is our SaaS-based control center. It provides policy definition, policy management, and policy evaluation. It's highly performant, highly reliable, and secure.
MCP Authorization Service:
The MCP Authorization Service leverages your human IDP to allow Aembit to create a "blended identity" that combines an Agent's non-human identity with the rights of the human interacting with it.
Policy Engine:
The policy engine allows you to create, activate, and deactivate access rights with a few clicks.
Trust Provider:
A trust provider is a federation relationship that allows Aembit to cryptographically verify the identity of an agent or workload via the platform where the agent is running, or another form of verifiable identity.
Credential Provider:
A credential provider is a federation relationship with target services such as an MCP server, a database, or a cloud resource. This relationshp allows Aembit to provide credentials on behalf of the target service, once a policy-based access request has been approved.
Admin Logs:
Admin logs track changes to your Aembit environment, including adding/removing users, modifying policies, and adding new resources. These can be easily exported to your SIEM.
Metrics:
Metrics create Aembit's dashboards, allowing operators to easily understand how the environment is performing.
Authorization Events:
Authorization Events are identity-based logs that show each approved or denied authorization attempt with reasons. It's all based on the client's identity, making audit simpler. These can be easily exported to your SIEM.
Easy Aembit Setup:
Aembit is designed to be integrated into your systems to run at production speed and scale via infrastructure as code. Easily use tools like Terraform to comfortably let Dev and DevOps manage Aembit.
Human IDP:
To create a "blended" AI Agent Identity, Aembit combines the distinct identity of the agent (derived from the Trust provider) with the rights of the human that's using the agent. The human rights come via an integration to your Human IDP.
3rd-Party Vaults:
Aembit can either mint short-lived credentials, vault them, or pull credentials from an existing vault like Amazon Key Manager, Azure Key Vault, or HashiCorp Vault.
Conditional Access Sources:
Aembit pulls contextual information from existing tools such as Crowdstrike Falcon or Wiz to assess operating characteristics of your AI agents and Workloads, before giving them access to your sensitive data and systems.
SIEM:
Aembit is designed to easily integrate with existing tooling like Splunk, Crowdstrike SIEM, or Snowflake. Easily output authorization events and admin logs directly to your system of record.
Real-Time Access Enforcement:
Aembit provides real-time enforcement of access requests based on identity of the agent or client workload, conditional access, and a defined policy of access rights. Based on approval Aembit delivers a credential in real-time.
DevOps and Security have a single place to enforce, manage, and log access, with no developer burden through no-code auth.
A single IAM platform so your agents & workloads can interact across data centers, clouds, SaaS services, and third-party APIs or MCPs.
“Identity is the cornerstone of Zero Trust. Today robust workload IAM is out of reach of all but the most sophisticated organizations. Aembit is democratizing workload IAM for all enterprises.”

“Aembit is a game changer! Along with making us more secure, Aembit also helps automate existing processes. We estimate that Aembit can save us 5-10 hours a day.”

“Securing workload identities is the foundation of a secure by default approach to security. Aembit provides an elegant approach that works across clouds, containers, APIs and SaaS services.”
Whether you are building custom agents on your own or leveraging an agent platform, Aembit provides multiple integration methods so that you can always easily verify the identity of agents anywhere.
















Wherever you build, Aembit will be there to support you. Your client workloads can live in a range of different environments that we support out of the box.
Workload authentication uses a range of approaches, and our goal is to help you uniformly support them all.












Wherever you’re connecting, we’ll make it easy for you with our out-of-the-box integrations with the most popular APIs and Services. This list is always growing, and we work with you as you need specific workloads.
Grant access based on additional, dynamic and configurable characteristics of workloads such as security posture, time of day, workload geography and more.
Get started in minutes, with no sales calls required. Our free- forever tier is just a click away.