Traditional approaches to secrets management often lead to challenges like secret sprawl, accidental exposure, and difficulties in rotating secrets without disrupting operations.
Secrets managers have completed their job once they deliver secrets to client workloads. However, many questions need to be answered:

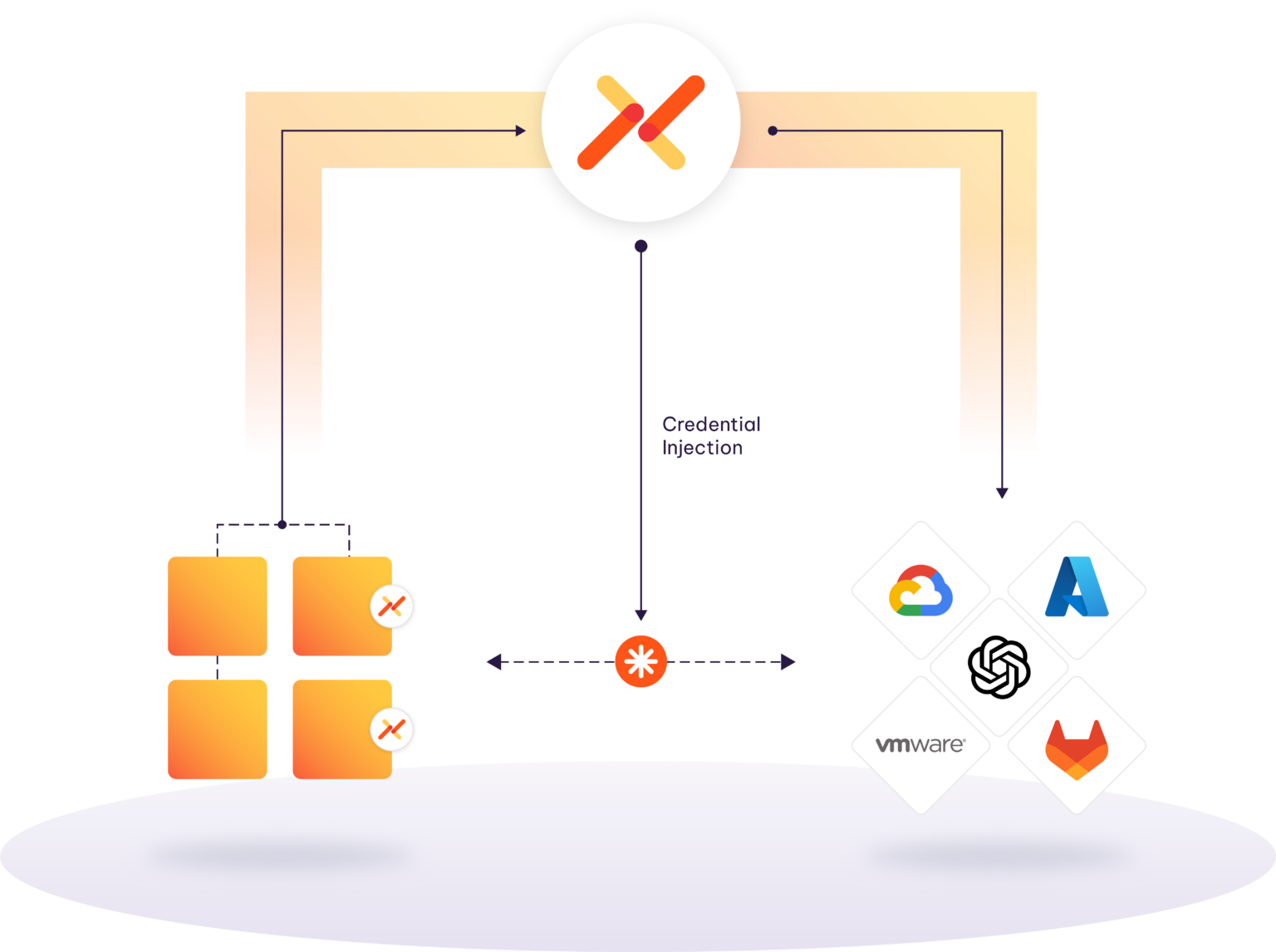
Aembit’s objectives are very different from the secrets managers. We ensure that only authorized client workloads can access server workloads.
We solve secrets management, and also solve inconsistent authentication implementation problems, mitigate the risk of client workloads leaking secrets, and the need to adhere to security best practices.
Aembit’s platform removes the need for secrets management by providing a secretless and automated solution for workload access.
By replacing long-lived credentials with temporary, just-in-time access rights, Aembit reduces the risk of secret leakage and unauthorized access.
Automate access the same way you do the rest of your infrastructure. No more manual provisioning and management of secrets.
Improve management efficiency by setting policies, based on both identity of a job and dynamic conditions. Eliminate the need to manage low level credentials.
Eliminate the need for developers to build and manage auth within applications. Implement a single, consistent approach.

