Eliminate hard-coded and long-lived credentials – and build truly resilient software deployment pipelines – with a unified identity system across clouds.
Non-Human IAM
Automated, policy-enforced access for your workloads and AI agents.
Workloads are connecting everywhere – but non-human identities still cling to static, long-lived credentials that end up in the wrong hands and in the wrong places.
of access today is non-human, and growing fast
secrets leaked on GitHub in 2024 alone
of access today is non-human, and growing fast
of non-human identities are over-permissioned
of ex-employee tokens stay active
of access today is non-human, and growing fast
secrets leaked on GitHub in 2024 alone
of access today is non-human, and growing fast
of non-human identities are over-permissioned
of ex-employee tokens stay active
of access today is non-human, and growing fast
secrets leaked on GitHub in 2024 alone
of access today is non-human, and growing fast
of non-human identities are over-permissioned
of ex-employee tokens stay active
Deliver access credentials anywhere – consistently and securely – with built-in identity verification, policy enforcement, and MFA-level controls for apps, services, and AI agents.
Aembit is designed to provide you flexible, performant, and reliable identity and access management for workloads without the heavy developer lift of deploying open source identity tools or the overhead of complex vaults.
No secret sprawl, and no new certificates to rotate. Workloads continuously authenticate via existing identity sources and receive just-in-time access.
Define what workloads can access with policies enforced in real-time — no scripts, no manual workflows, no surprises.
Flexible authentication across AWS, Azure, and GCP, On-prem and SaaS — without deploying new identity systems. Use Oauth, OIDC, SPIFFE, Kerberos, and more.
Aembit Edge integrates transparently into workloads — no rewrites. Or choose from our CLI and API deployment models for complete flexibility.
Audit access in real-time — without requiring external monitoring or custom logging.
SaaS-delivered, SOC2 and ISO27001 certified. Highly available, reliable, and scalable. We don’t require dozens of add-ons and extensions for basic functions. Built and supported by a dedicated global team.
Automate access the same way you do the rest of your infrastructure. No more manual provisioning and management of secrets.
Aembit replaces long-lived credentials with temporary, just-in-time access rights. No risk of secret leakage and unauthorized access.
Works in any cloud, across SaaS, even on-prem. Multiple auth types, a range of credential types, and no management. Aembit lets devs get back to work.
Use policies to ensure that only cryptographically verified non-human identities can access sensitive data and infrastructure.
Provide a single source of intelligence to confirm workload-to-workload access reviews. Prevent protracted reporting and analysis cycles.
Support billions of transactions. Designed to scale by orders of magnitude more.

“Identity is the cornerstone of zero trust. Today robust workload IAM is out of reach of all but the most sophisticated organizations. Aembit is democratizing workload IAM for all enterprises.”

“Aembit is a game changer! Along with making us more secure, Aembit also helps automate existing processes. We estimate that Aembit can save us five to 10 hours a day.”

“Securing workload identities is the foundation of a secure by default approach to security. Aembit provides an elegant approach that works across clouds, containers, APIs and SaaS services.”
FEATURES
Aembit boosts security by cryptographically verifying workload identities, in real time, ensuring that only trusted workloads have access to your sensitive data.
Aembit injects short-lived credentials into requests just-in-time so you never have to store or protect access secrets. Aembit uses identity federation to eliminate the need for stored identity secrets.
Dynamically enforce access rights based on real-time evaluations of workload security posture, geography, time windows and other key behavioral characteristics.
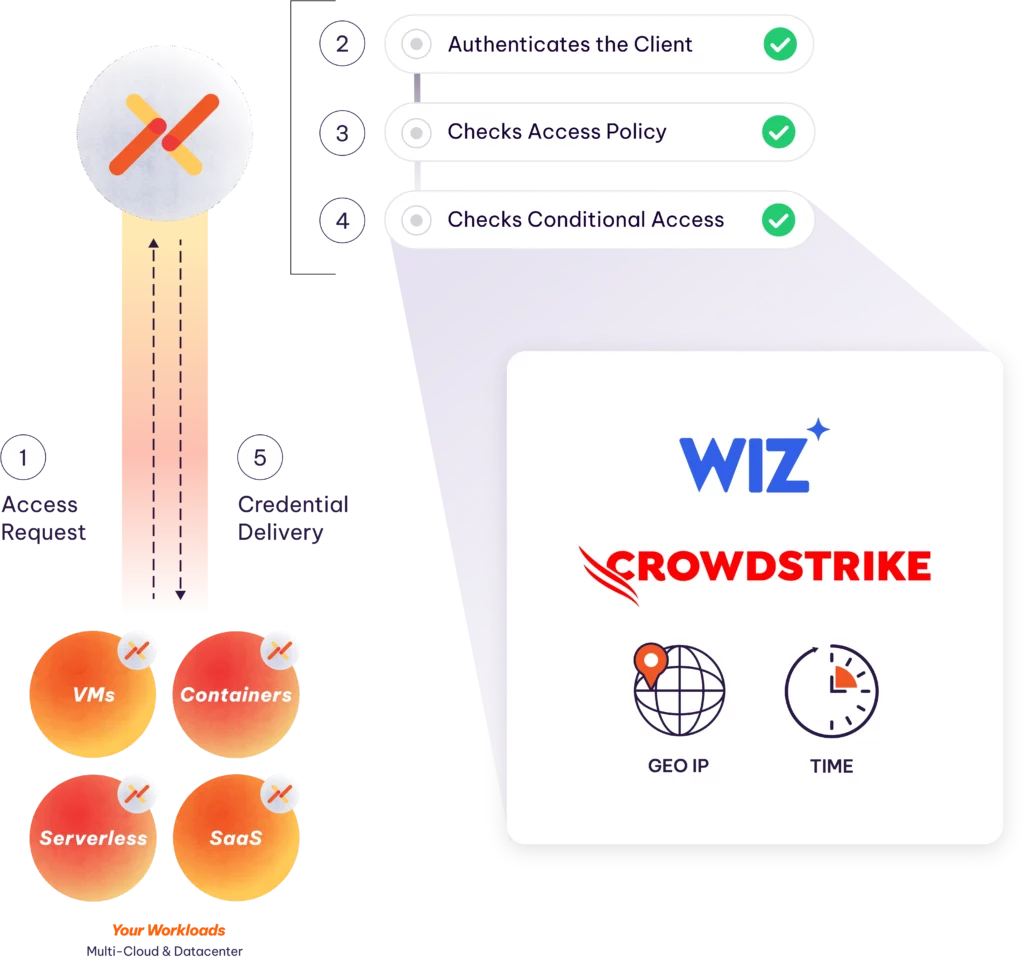
Aembit is an independent identity broker that can secure access among clouds, SaaS, and on-premise data centers.
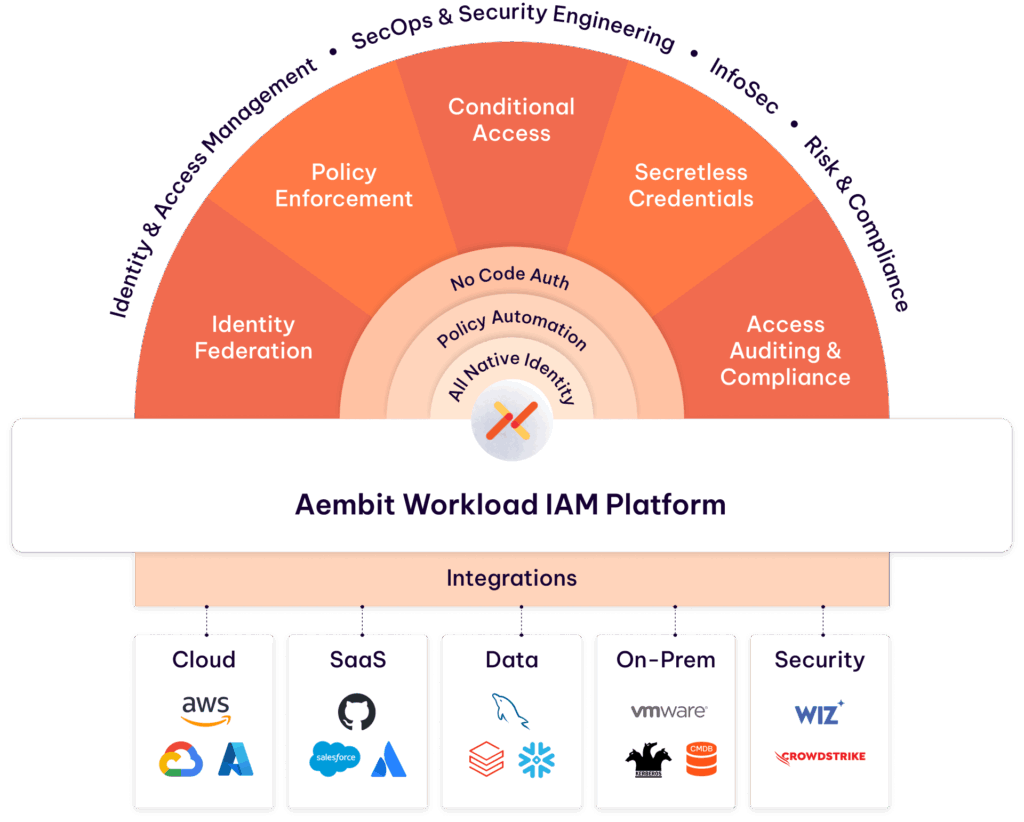
Aembit provides detailed centralized that discover workloads and provide audit logs of their access to sensitive resources.
Eliminate hard-coded and long-lived credentials – and build truly resilient software deployment pipelines – with a unified identity system across clouds.
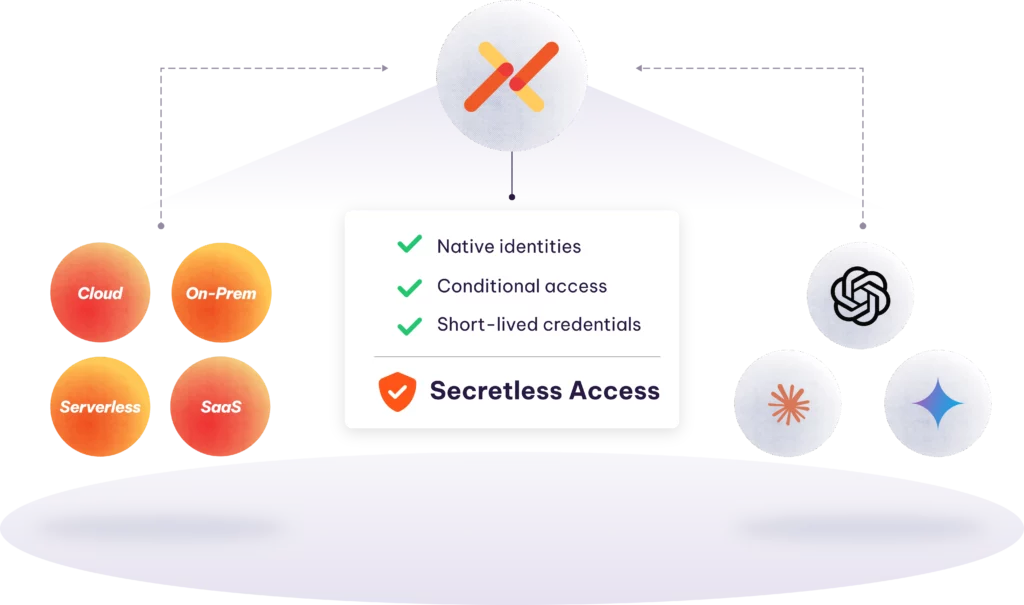
Simplify and control access from AI agents to leading LLMs like OpenAI, Claude, and Gemini with policy-based, identity-driven security.
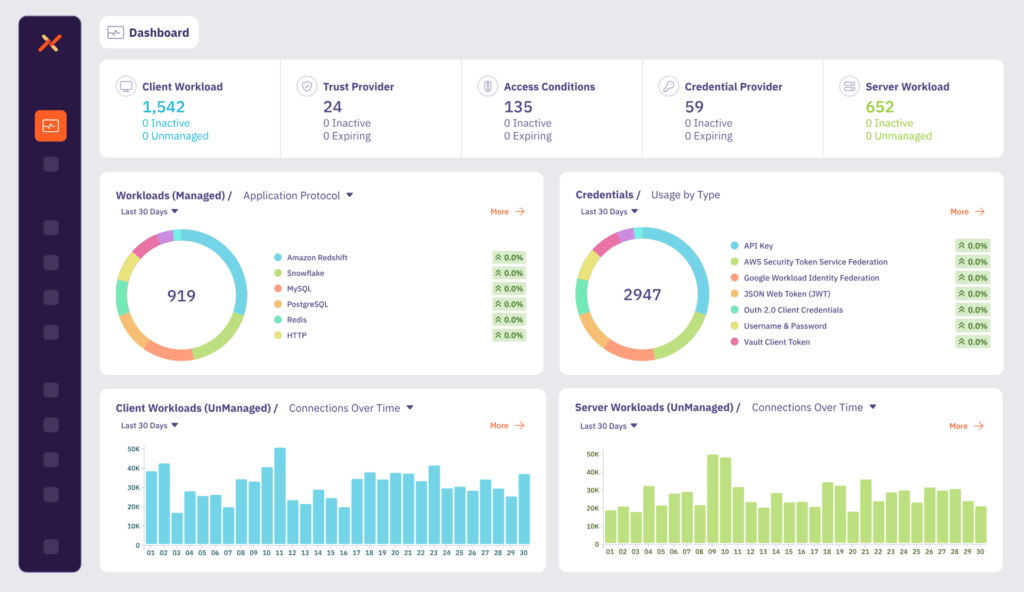
Explore real-world ways customers are scaling and securing workload-to-workload access across their environments with Aembit.

“Aembit is a rising star in the Non-Human Identity and Access Management space, offering an innovative approach to securing workload identities. Its focus on secret less authentication, dynamic access control, and Zero Trust principles makes it a strong contender in this emerging market.” Read more
Get started in minutes, with no sales calls required. Our free- forever tier is just a click away.