Introduction: Why AI Agents Need Identity and Access Management
AI agents are starting to handle real work—looking up customer data, creating tickets, summarizing logs, and even triggering changes in your cloud infrastructure. Agents need access to your most sensitive data and critical systems to be useful. Just like humans, access is the first line of defense; and who agents are determines what they can do. Most enterprise guardrails were built for people, not for fast‑moving software actors that spin up for seconds, act independently, and chain across tools.
With the speed of AI adoption, friction is rising: security teams can’t meet compliance and risk requirements, and development teams take on overhead to implement authentication when they want to ship features.
With Aembit’s new IAM for Agentic AI, security teams can responsibly provide and revoke access to sensitive data and resources based on agent identity and centralized policy. And, since Aembit is no-code, security teams can reduce identity security overhead on development teams.
We’re excited to tell you more.
AI Access Problems Enterprises Face
No clear identity for the agent. Today, an agent’s access is often hidden behind a human’s identity—both in actions and the audit trail.
Secrets in the wrong places. Where agents use machine credentials, teams reach for the simplest (and least secure) form of access—secrets and API keys. If a key lands in the agent’s runtime, the agent can use it, pass it to others, emit it, and lose it to anything that touches that runtime.
Human processes don’t map. Joiner/Mover/Leaver and monthly rotations assume employees, not jobs that begin and end in minutes. Plus, human MFA doesn’t work for AI Agents.
Everything speaks something different. Agents speak MCP; targets speak OIDC, OAuth2, PATs, SSH certs, API keys, or database logins. Bridging that safely is hard. It drives developer overhead and weak accountability.
Boundaries everywhere. Agents in one cloud routinely need to access SaaS and on‑prem systems in another trust domain—each with different identity systems, policies, and credentials.
Auditing and attribution gaps. Without a distinct agent identity (and user context when present), logs collapse actions under a human’s token or “some agent,” undermining compliance, incident response, and root‑cause analysis.
Why This Matters Now
Pilots are becoming production. Leaders want efficiency; security and compliance need provable control. If you can’t allow access safely, you end up blocking broadly.
Early incidents aren’t just model errors. They’re access failures: unclear attribution, unscoped data pulls, stale tokens used by “some agent”, and weakening of controls to just make access work.
Security can block or enable. AI is moving. Security can enable developers with confidence or slow adoption.
Aembit: The 5 Requirements of IAM for Agentic AI
Working with real customers—a Fortune 250 retailer, a top government security contractor, a leading AI agent platform, and a highly regulated financial services company—Aembit formed a clear view of what enterprises need to protect data and systems in agentic workflows.
We’re introducing two new capabilities—blended identity for AI agents and an MCP Identity Gateway—combined with our enterprise‑class Workload IAM foundation to achieve these five things:
- Treat the agent as a first‑class, distinct identity, and add user context when present. Leverage the agent’s environment to provide dynamic identity and conditional access at the scope, scale, and velocity of agents. Bind upstream human context when the agent acts for someone.
- Enforce runtime access at a clear control point with a well-defined policy and issue secretless, just‑in‑time credentials that expire quickly.
- Enable a kill switch so security can quickly revoke access if an agent behaves erratically.
- Translate credentials safely across SaaS, cloud, and on‑prem targets without exposing creds to the agent.
- Provide clear attribution within audit logs—per agent, per user binding, per tool—without downstream rewiring.
Aembit issues ephemeral credentials after policy evaluation—no long‑lived keys in code and no vault lookups in agents. Access is short‑lived and configurable. Policies translate across clouds, data centers, and SaaS, giving you one control point for modern and legacy protocols. Developers get a zero‑code path to secure access; security teams get zero standing privilege with full auditability.
Meeting the Needs of IAM for Agentic AI
As we worked with clients on AI deployments, two challenges emerged:
- How to give an AI agent an identity dependent on both the agent software and the human interacting with it?
- How to provide least privilege along the entire access chain—ensuring the agent and the MCP server have only what they need?
Here’s how we solved this.
Blended Identity: A First‑Class Identity for the Agent, With Upstream Human Context
We’re releasing Blended Identity.
Agents aren’t people—and yet often act for people. Blended Identity gives each agent a first‑class non‑human identity, then optionally binds a user context so access can be scoped and audited with attribution. Our design treats the agent as its own workload identity, then binds upstream human context when the agent acts on someone’s behalf.
Outcomes
- Ability to enforce an access policy based on the blended identity. The policy is defined as a least privilege authorization based on the blended identity of the agent and the user.
- Attribution that distinguishes an agent acting for a user from a user acting directly.
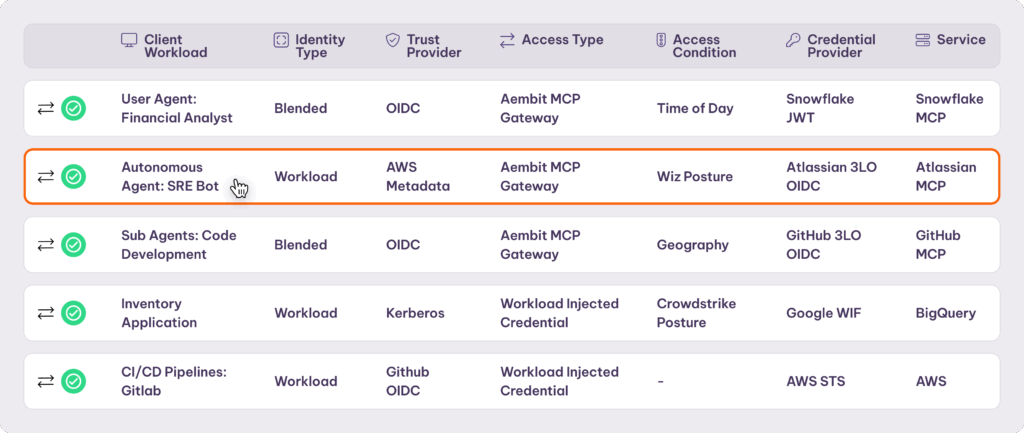
How We Implemented It — MCP Authorization Service & Human IDP Integration
When an agent (in container, VM, function) requests access, Aembit dynamically attests to workload identity via cryptographically verifiable documentation from the environment (e.g., AWS metadata document, Kubernetes service account token, OIDC token, Kerberos ticket). Agents never handle bootstrap secrets—the “Secret0” problem is removed.
For user‑driven agents—where the agent receives directions via a user interaction—we bind the agent identity with optional user context: the authenticated human (IdP claims, group/role attributes, purpose‑of‑use, ticket ID). Additional context comes via conditional access attributes: execution metadata (agent posture, time of day, geography), and tool name, model, chain step, or other risk signals.
When user context is present, we propagate only the minimum required attributes downstream to define scope. Every access log includes both agent identity and, if available, user_context so audits can always tell “agent acting alone” vs “agent acting for Alice.”
Blended identity is enabled by two elements:
- An MCP authorization service within Aembit, whereby customers can redirect their on-premise or SaaS MCP servers to use Aembit for authorization with a line of configuration.
- Integrations with human IDPs, where we pull context on humans, groups, and roles. Aembit isn’t your workforce IDP; it focuses on the identity and policy to control access for the agent or workload. We consume data from your workforce IDP and bind it to the agent’s operating context.
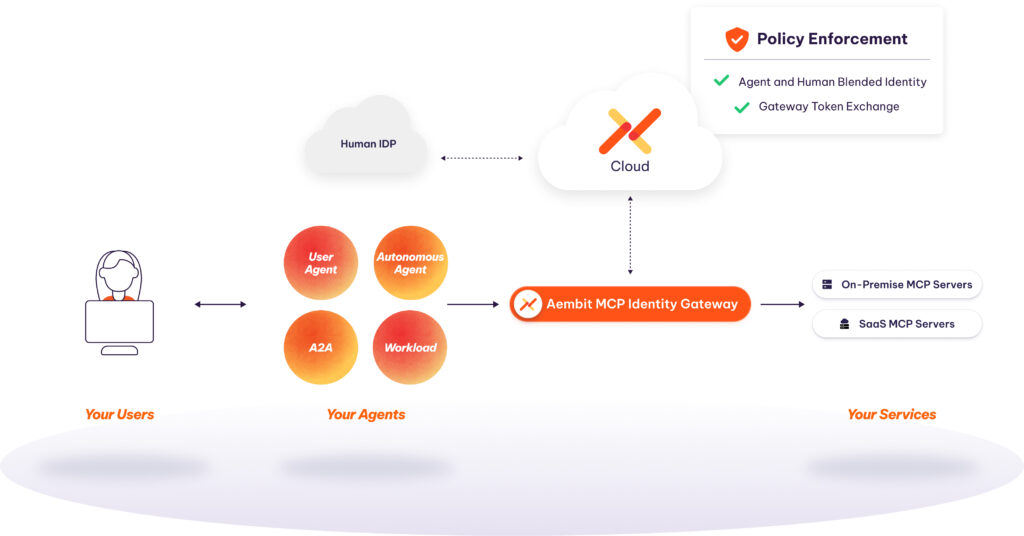
MCP Identity Gateway: Identity‑Aware Termination and Token Exchange
Instead of giving an agent credentials with rights to access services directly, we split the flow into two phases: authenticate the agent and user and issue a blended identity credential that the agent uses to authenticate to the MCP Identity Gateway. The gateway uses token exchange to obtain the correct access credential for the target and returns that credential to the MCP server to access the service. The agent never receives the access credentials. This model works for both enterprise-owned custom MCP servers and 3rd party SaaS MCP servers.
- Policy evaluation: Before any MCP tool call executes, Aembit evaluates policies against the blended identity and run context (resource, parameters, time, geo, risk). If allowed, it proceeds; otherwise, it blocks and records a structured denial with reasons.
- Token exchange: When Aembit attests to the agent identity, it issues an identity credential usable only at the gateway. The gateway, working with Aembit Cloud, exchanges it for the exact access credential the target expects—short‑lived and audience‑scoped when possible.
- Examples: mint an OIDC access token for a SaaS API with claims reflecting user department + agent role; generate a temporary DB login; produce a one‑time PAT/API key for legacy tools that can’t consume OIDC.
What This Enables
- Policy-enforced access, with just-in-time credential delivery: the agent never sees or stores long‑lived credentials; nothing sits in files, env vars, or prompts.
- Cross‑boundary access that “just works”: an agent in AWS can call an MCP tool that hits Snowflake, Salesforce, or an on‑prem DB—each with the right ephemeral credential and least‑privilege scope.
- Provable attribution: every tool call is bound to who/what/why at the moment of use, tracing the upstream context—human or another agent.
Better Together: Blended Identity + MCP Identity Gateway
While the MCP Identity Gateway is essential for securing third-party tools, it provides the ultimate security architecture when combined with our MCP Authorization Service for your own applications.
In this model, you configure Aembit as your Authorization Server and write a simple, powerful policy: ‘Only issue access tokens to the MCP Identity Gateway.’ This forces all traffic, internal and external, through a single, auditable data plane. You get the rich user context of Blended Identity combined with the real-time policy enforcement, token exchange, and credential isolation of the Gateway—all in one seamless flow
Workload IAM Foundation: Policy, Enforcement, and Auditable Runtime Control
Your AI stack is only as powerful as the data it can access. That data lives in distributed, heterogeneous systems built on existing patterns. An AI‑native access platform must understand these patterns.
Under the covers, our new capabilities leverage the hardened Workload IAM fabric we run at scale for non‑AI workloads—redesigned for agentic patterns.
Central Policy Plane, Distributed Enforcement
- Policy enforcement using attributes from the agent, resource, and environment. Enforcement happens at the host/cluster edge via our transparent proxy/sidecar for zero‑code adoption or in‑process via lightweight SDK. Now we’ve added the MCP Identity Gateway as an enforcement point.
- Zero Standing Privilege (ZSP). Access is granted only at request time, after policy evaluation, materialized as a short‑lived credential with pinned audience, scope, and TTL.
- Conditional access (like MFA, but for agents). Policies can require stronger attestation of the agent runtime (signed image, security posture, geolocation).
- Kill‑switch. Block specific agents with a simple policy change; with short‑lived credentials, blocking is nearly immediate.
- Unified audit with attribution. Every decision (allow/deny), JIT credential issuance, and downstream call is a structured event tied to the agent and optional user context. These records power compliance (SOC2/ISO), incident response, and granular cost/usage analytics.
Developer & Ops Integration
- Zero‑code on‑ramp. Drop in the host‑based proxy; we intercept, identify, and enforce.
- CLI & SDK options. For scripted agents or where you want explicit calls, the CLI and SDK provide the same identity bootstrap and JIT flows.
- Heterogeneous environments. Works across Kubernetes, Virtual Machines, serverless functions, laptops (for local tools), and hybrid networks.
- Varied authentication protocols and credential types. OAuth, Amazon/Google/Azure Short Tokens, JWTs, API Keys, Username/Password, SPIFFE, for example, are supported. And the list keeps growing.
It’s this combination of powerful enforcement, visibility and developer simplicity that makes IAM for agentic AI and workloads so powerful.
Summary: Accelerate AI Adoption Confidently
Our customers are telling us that Aembit IAM for agentic AI does more than just protect enterprise resources. With the ability to confidently protect those resources, businesses can truly innovate and explore the power of agents. With Aembit, enterprises have:
- A central runtime control point to allow, constrain, or kill AI access—without chasing secrets across agents, tools, and clouds.
- Agent velocity (no auth code, no key wrangling) with least‑privilege, zero‑standing‑privilege guarantees.
- Auditable attribution for every action, unified across agentic AI and existing non‑AI services—one model, consistent controls.
Ready to get started? Contact us to try IAM for Agentic AI today. Sign up to start using our Workload IAM platform now.
Ready to Try Aembit?
Get started in minutes, with no sales calls required. Our free- forever tier is just a click away.




