We’re excited to announce our direct integration with Splunk, a leading SIEM platform trusted by enterprises worldwide.
This powerful integration enables security teams to gain deeper insights by bringing workload identity and access information directly into Splunk’s robust analytics environment.
By streamlining event correlation and accelerating incident response, this collaboration empowers organizations to stay ahead of evolving threats while maximizing the value of their existing security investments.
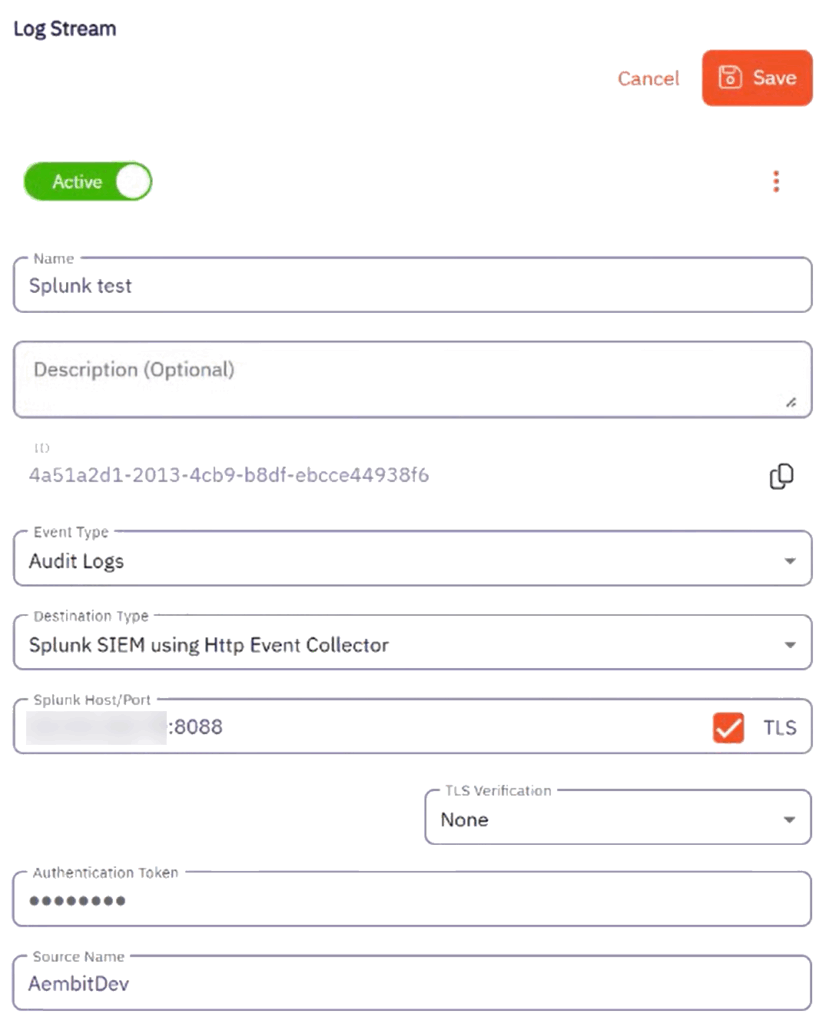
As with all Aembit integrations, the configuration is simple.
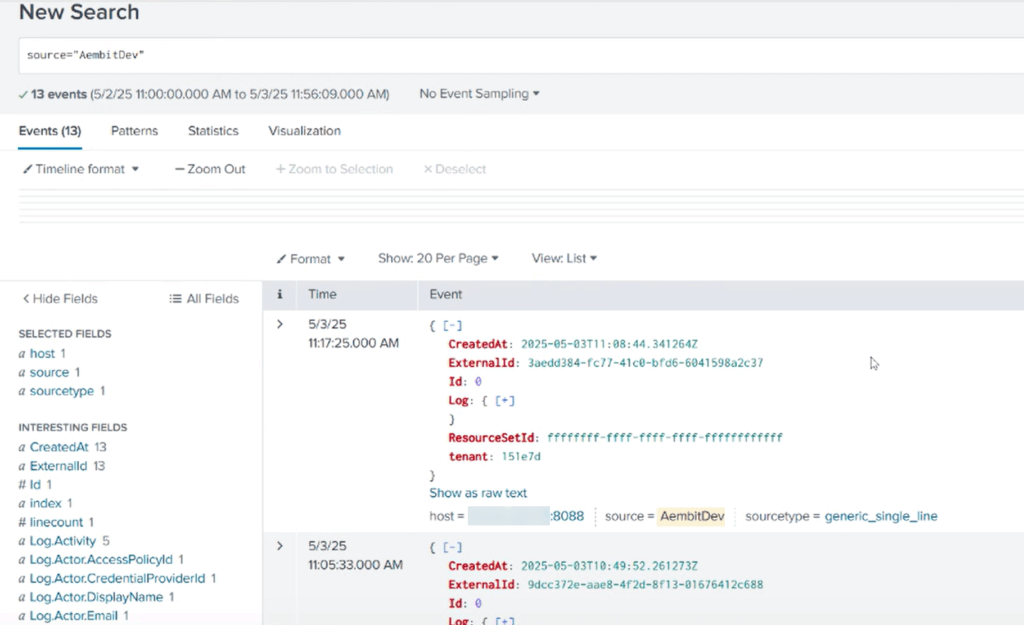
Aembit generates logs in standards-based JSON format, making them easily consumable by Splunk’s powerful indexing and search capabilities.
This structured logging approach ensures compatibility with existing Splunk workflows, allowing security teams to apply familiar filtering, correlation, and alerting rules without the need for custom parsers or complex transformations.
Whether you’re leveraging Splunk’s native dashboards or custom-built Splunk apps, Aembit’s JSON-formatted logs can be seamlessly integrated to enrich threat detection, enhance audit trails, and support compliance reporting — all while fitting naturally into your existing data pipeline and operational tooling.
Using Aembit in combination with Splunk gives organizations powerful visibility and control over how workloads are being accessed and used across their environments. Aembit Edge can passively discover workload-to-workload communication, identifying which services are talking to each other, when, and under what conditions.
These insights are streamed into Splunk, where security and operations teams can use dashboards, queries, and alerts to better understand access patterns, detect anomalies, and ensure that workload behavior aligns with policy and compliance expectations.
But beyond visibility, the integration also empowers action. Teams can go a step further by programmatically interacting with the Aembit API to manage workload access in real time.
For example, based on observed usage or triggered events, Splunk can generate access policy recommendations or automatically create access policies in Aembit to restrict, allow, or modify connections between specific services — turning insights into enforceable security controls.
The Splunk integration can also assist in modernizing access workflows by generating IT tickets when unmanaged workloads are discovered. These tickets can prompt teams to onboard new workload objects into Aembit and migrate from insecure static API keys to Aembit’s short-lived, identity-based tokens.
This reduces long-term credential sprawl and aligns with zero trust principles by ensuring that all workload access is authenticated, authorized, and continuously monitored. The integration is continuously monitored by Aembit, and if Log Stream failure is detected, it automatically sends administrators an email notification.
Aembit also continues to support Splunk integration by enabling customers to export logs to an AWS S3 bucket or a Google Cloud Storage bucket, which Splunk could then ingest using tools like Splunk Data Manager or Splunk Add-on for Amazon Web Services.
This approach provides a functional pipeline for getting Aembit data into Splunk. It may be preferred for organizations already leveraging cloud storage workflows for log centralization and works well with existing infrastructure and compliance practices.
Aembit provides both methods to easily adapt to your organization. To learn more about direct Splunk streaming, visit https://docs.aembit.io/administration/log-streams/splunk-siem.