While Microsoft has been around for a long time, the security of workload and machine-to-machine access in Microsoft and Azure environments is complex, inconsistent, and hard to manage.
Transitioning from on-premises to cloud, either Azure, AWS, GCP and beyond, demands secure authentication, synchronized identities, and policy enforcement across platforms. Ensuring compliance and visibility across both environments can be complex.
Entra ID, conditional access, and role-based access control help, but legacy systems and differing protocols often hinder seamless integration.
Migration also requires careful workload mapping and maintaining application uptime during transitional phases.
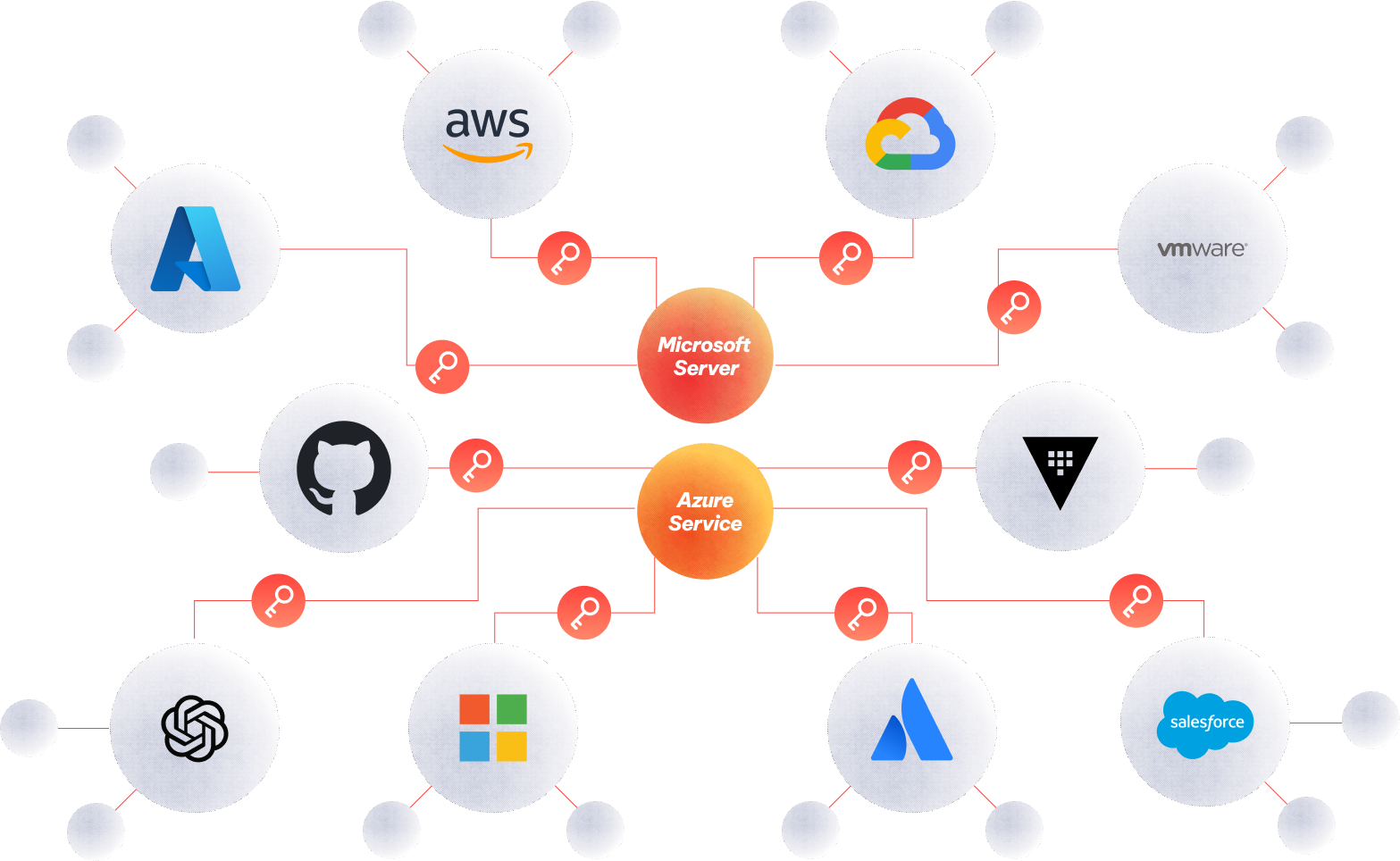
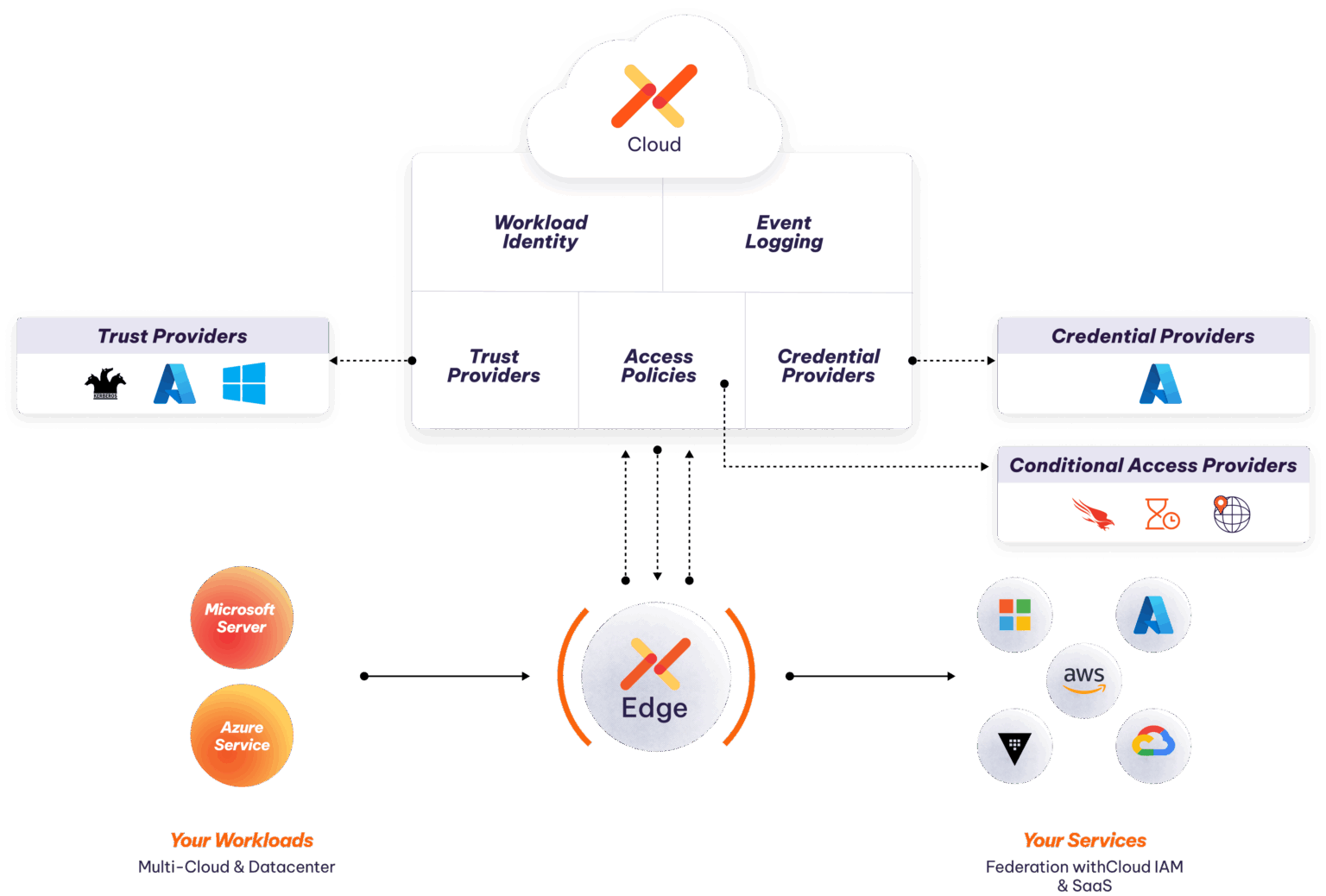
Aembit helps secure organizations’ workloads by providing secure, identity-based access for machine-to-machine communication across Microsoft on-premises, Azure, or hybrid environments. It eliminates the need for hardcoded credentials, dynamically authenticating workloads using existing identity providers like Entra ID and WIF.
Aembit supports workloads, credential providers, and trust providers across both on-premises and Azure while other solutions only offer some functionality on cloud and completely ignore anything on-prem.
For organizations migrating to Azure, Aembit ensures consistent access policies and secure transitions by abstracting authentication from the underlying infrastructure. This reduces operational complexity, strengthens security posture, and supports a smoother, safer shift from on-premises to cloud-native architectures.
Aembit unifies identity-based workload access across Microsoft on-prem and Azure environments—without relying on static secrets or inconsistent legacy controls.
Aembit's integration with Microsoft and Azure is smooth, and offers multiple methods of integration with workloads that are also accessing your server and services.
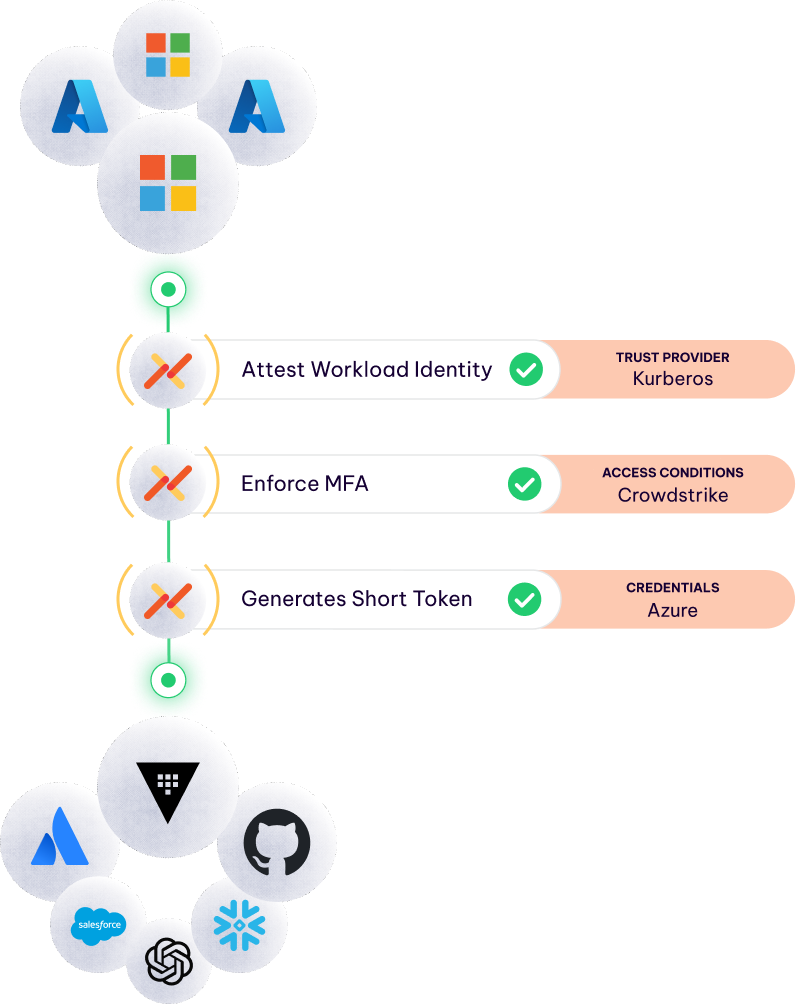
Accept and validate identities from almost any environment (cloud, SaaS, on-prem) and seamlessly translate that to a valid Microsoft access credential.
Get MFA-like strength by combining identity, policy, and conditional access to check security posture, geo-location, and even time of day.
Improve management efficiency by setting policies, based on both identity of a job and dynamic conditions. Eliminate the need to manage low level credentials.

