Aembit now supports client workloads running in virtual machine environments, both cloud and on-premises, in addition to supporting Kubernetes.
This enables a broader spectrum of workloads across various environments to establish secure connections – based on identity and policy – to cloud-native and Kubernetes-based workloads, across trust domains.
As always, Aembit secures access from these workloads to a range of target services, including databases and data warehouses, SaaS services, third-party APIs, as well as other custom and packaged workloads in the same or different cloud environments.
This will accelerate the adoption of cloud-native architectures, because you can more easily and more securely access the VM-based and legacy applications that your enterprises depend on, even if you are not migrating to a cloud-native stack anytime soon.
As organizations increasingly embrace containerization and cloud-native architectures, Kubernetes has become the go-to platform for deploying and managing workloads across environments.
When we launched Aembit, starting with support for Kubernetes was a natural insertion point given its modern architecture and the inherent need for workload identity and access management (IAM) across trust boundaries.
As our approach gained traction, customers have increasingly embraced our vision of access management: a unified workload IAM platform across all of their workloads and their compute environments.
As the next step in achieving this vision, we are happy to announce that we have extended support for workload IAM from Kubernetes environments to virtual machines. For our customers, this means you can now manage access, not secrets, across all of these environments consistently.
Aembit eliminates the need for static, long-lived identity secrets, removes the requirement for developers to code auth, and consolidates control and visibility so you can aggregate workload interaction logs in a consistent format for improved analytics, compliance, auditing, and risk reduction.
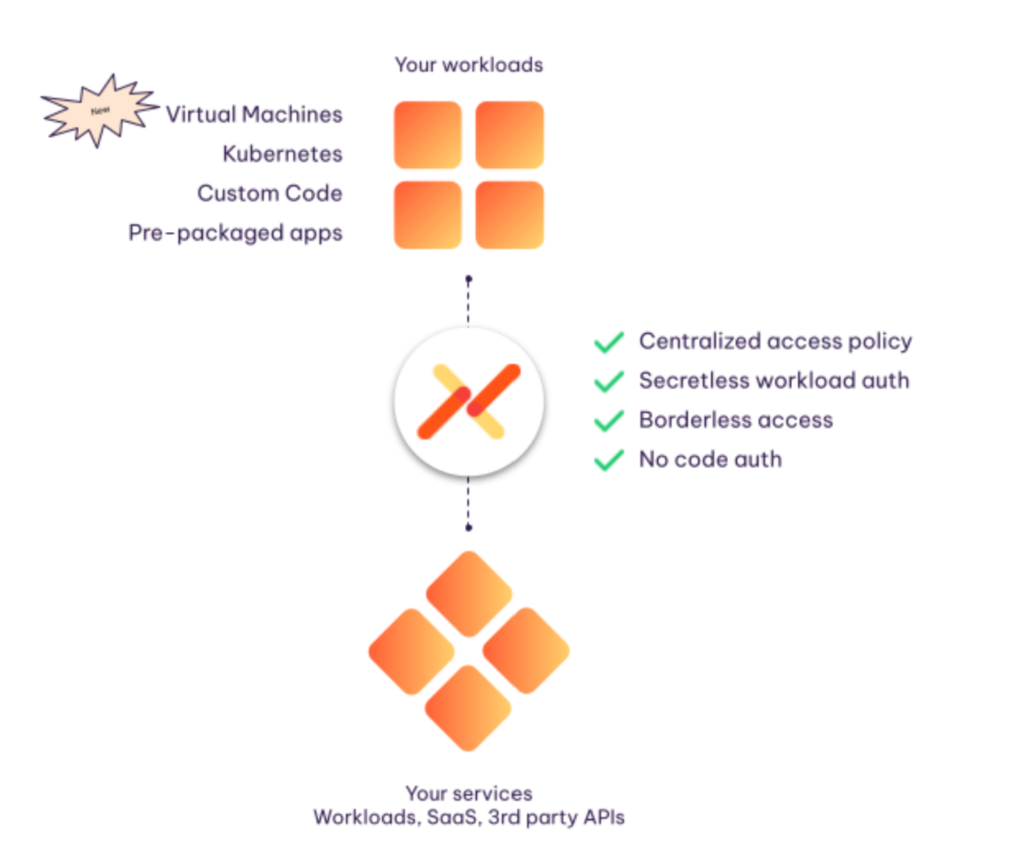
The Significance of Extending Workload IAM Support
Organizations have multiple ways of managing workload-to-workload access. This, in fact, is the problem: Enterprises must use multiple access management techniques because a single approach cannot support their range of environments, nor will it allow the organization to effectively manage access across boundaries from one cloud to another, or to a SaaS service or third-party API outside of their domain.
But to treat workload IAM as an issue you can solve for on an environment-by-environment basis misses the larger point: Organizations would be better served via a workload IAM platform that can provide a single approach to connect a range of trust domains, operating systems, platforms, and even third-party services with which your applications interact.
Core Benefits of Our Approach
- Interoperability, Served Three Ways: Let’s face it: Most enterprise environments are complicated, use disparate technology, and require workload identity infrastructure to support it. For workload identity, that means providing the ability to support variety, but also brokering IAM across different environments:
- Both containers and VMs.
- Workloads (apps or APIs) that live within your trust domains, and SaaS services that others operate.
- On-premises and cloud.
- Flexibility: Some workloads are best suited for VMs due to their specific requirements. By extending support to VM environments, Aembit enables organizations to choose the right technology for their specific use cases without compromising on IAM security.
- Secrets Management and Service Account Sprawl: Aembit dramatically reduces secrets sprawl – applications no longer need to hard code or even temporarily store keys. Similarly, access is governed by Aembit, giving you a single place to manage and audit use of service accounts. These two benefits greatly simplify operations complexity for ongoing maintenance, as well as incident response activities.
- Security: Aembit provides policy-based and conditional access to applications and services based on identity, and not just secrets. Extending support to VMs ensures that organizations can enforce consistent security policies across multiple environments.
- Comprehensive Auditing and Compliance: Aembit’s extended support includes robust auditing capabilities to track and report on access and activity in both VM and Kubernetes environments, facilitating compliance with regulatory requirements. Logs will look the same across environments.
How to Extend Your Aembit Deployment to VMs
The most important change in this release is the ability to set up Aembit Edge on a VM. We’ll dig in there first, and then tie it in to the rest of our Workload IAM platform.
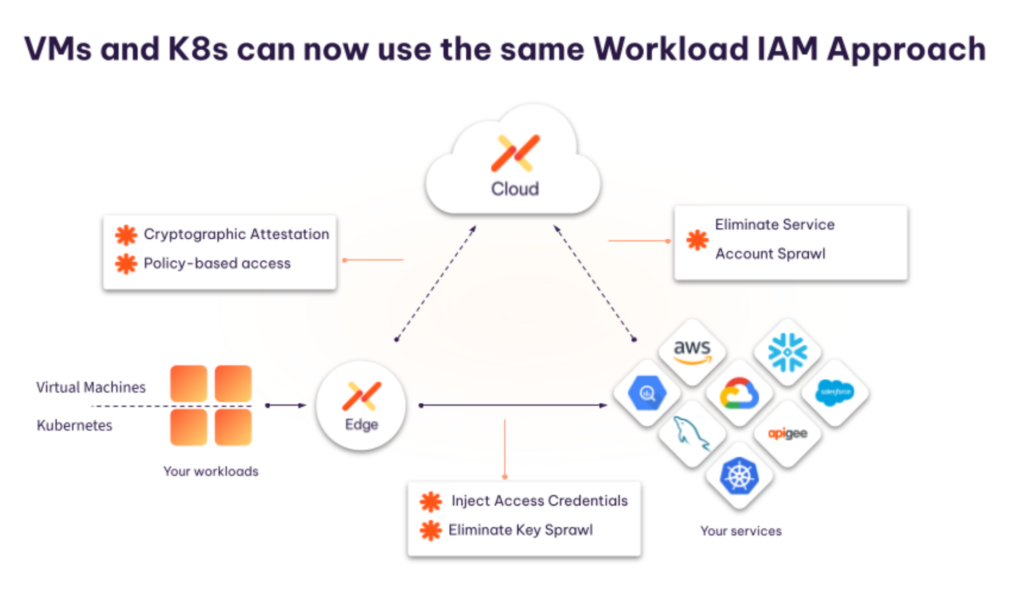
Aembit Edge for No-Code Auth
The Aembit Edge is our proxy deployed next to your workloads. In Kubernetes, it is deployed as a sidecar, but on a VM it’s deployed as an agent. It provides a transparent way for Aembit to validate workload identity and inject access credentials, without any changes to your existing applications. (Your developers will be happy about this.) Aembit provides downloadable installers, and the process can be automated through your configuration management tools.
While in Kubernetes, your workloads are naturally isolated. In VMs, Aembit Edge can discover client workloads as processes. Discovery is based upon their communication with services and the configuration to identify them based on the collected process metadata such as name, IDs, user, and group.
Aembit Edge applies access control and enforcement individually to these uniquely identified workloads based on the policy configuration, meaning that you can isolate and manage the important workloads as you see fit.
Once this is in place, the rest of the solution works as it does on Kubernetes today.
Unified Control Plane
Aembit provides a unified control plane for Workload IAM that uses identity to authorize access policies across many different environments. This simplifies management by offering a single interface for policy creation, access control, and auditing. Operators set up a one-time trust provider relationship between Aembit Cloud and your operating environment to help identify workloads. There is no change in policy creation.
Cross-Environment Identity Federation
Aembit can federate identities across different environments, ensuring that users and services can access resources securely, regardless of whether they are hosted on VMs or Kubernetes.
Benefits for Organizations
The extension of Aembit’s Workload IAM support to VM environments offers numerous benefits for organizations:
- Consistency: IAM policies can now be consistently applied across all workloads, reducing the risk of security gaps.
- Ease of Management: Security and DevOps teams can manage IAM from a single point of control, simplifying administrative tasks.
- Cost-Efficiency: Tasks like credential rotation, service account management, workload access auditing, and incident response become simpler and more efficient, allowing your DevOps teams to focus more on initiatives that move your business forward.
- Improved Security: By implementing IAM policies consistently, organizations can strengthen their security posture in a number of ways to better protect their data and assets:
- Become identity based, versus secrets-based access.
- Migrate from long-lived secrets to short-lived access tokens without developer lift.
- Control secrets sprawl.
- Control service account sprawl.
Availability
Aembit is creating a unified workload IAM solution that provides identity-based access to workloads across multiple clouds, on-premises, or to services run by partners and SaaS providers. In this release, we bridge the gap between Kubernetes and VMs, ensuring that workload IAM is a technology that addresses the reality of how organizations build, not just one that demands a homogenous environment.
Organizations can now confidently invest in Workload IAM, knowing that it will continue to support more environments and connect applications across a range of boundaries.
Aembit Edge for VMs is currently available for private preview and will be generally available later this year.
You are welcome to start with our free tier, which provides production-quality IAM for up to 10 workloads.




