Coming on the heels of our strategic investment from Okta Ventures, we’re proud to announce another significant milestone — the CrowdStrike Falcon Fund has also chosen to invest in Aembit.
This not only closes our seed funding round but furthers the cybersecurity industry’s confidence in our unique approach to Workload Identity and Access Management (IAM).
Like Okta, CrowdStrike has been a pioneer in its domain: stopping breaches, including endpoint and supply-chain attacks, ransomware, and malicious code, by employing cutting-edge techniques, including Zero Trust to understand the anatomy of an attack across endpoints, cloud resources, identities, and data.
CrowdStrike’s investment goes beyond the money and signifies a shared vision with Aembit: to extend Zero Trust to workloads, helping to close yet another increasingly common and concerning vector for threats and compromises.
In modern enterprises, the landscape of applications has become distributed and complex. From in-house developed software to third-party APIs and cloud-based services, this complexity makes it challenging to manage workload-to-workload access securely. Traditional approaches often rely on secret managers and brittle access mechanisms — methods that are both cumbersome and fraught with security risks.
CrowdStrike’s investment goes beyond the money and signifies a shared vision with Aembit: to extend Zero Trust to workloads.
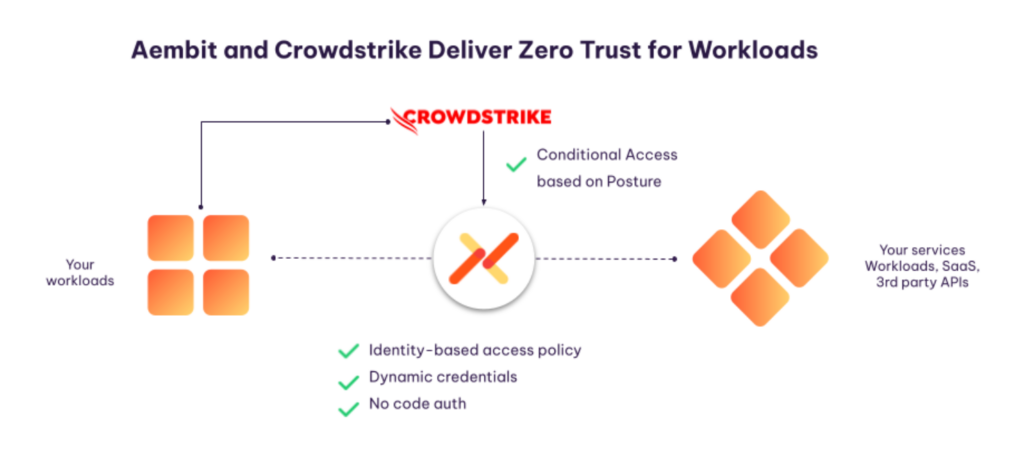
Incorporating Zero Trust into workload IAM is more than just a theoretical concept. It’s now a tangible solution. With Aembit, enterprises can cryptographically identify workloads and assess their security posture accordingly. This results in a more robust and efficient system, where conditional access policies are used to determine workload access rights, rather than rely on secrets (that may be long-lived, reused, and even hard-coded into applications).Our relationship with CrowdStrike will only deepen this capability.
What This Means for You
For our customers, you get to manage access, not secrets. Aembit eliminates the need for static, long-lived secrets, eliminates the need for developers to code auth, and consolidates control and visibility so you can aggregate logs in a consistent format for improved analytics, compliance, auditing, and risk reduction. And with CrowdStrike, you’ll be able to move toward a Zero Trust workload architecture that protects your most sensitive resources.
We’re exceptionally thrilled about the endorsements from CrowdStrike and Okta. It serves a resounding testament that we’re on the right path.
We have a lot more in the pipeline, including technical innovations and collaborative strategies. So, stay tuned for more updates as we take these significant strides together into the future of secure, identity-first workload management.
And remember, our basic tier is always free and allows a team to manage up to 10 workloads and access policies.