Aembit has added support for Microsoft Azure Entra Workload Identity Federation as a credential provider, further extending its universal identity federation capabilities.
This integration empowers non-human identities anywhere – whether in another cloud or on premises – to securely authenticate with Azure Entra ID, facilitating access to Azure-registered applications and managed identities without the overhead of relying on traditional credentials. Aembit simplifies Azure identity federation, removing the need for custom code in each application and reducing the burden on developers.
While a cloud service provider-specific Workload Identity Federation (WIF) works for a single cloud, it doesn’t work well when trying to federate across clouds. Also, WIF alone lacks certain capabilities that enterprises today require. This desired functionality, such as conditional access and workload verification and attestation – along with support for a broad range of credential types – is why pairing a WIF with Workload IAM is the stronger choice.
Azure identity federation is a feature that allows workloads running outside of Azure to authenticate to Azure services without the need for managing secrets or credentials. By federating identities from external identity providers (IdPs), such as Aembit, with Azure Entra ID, applications can obtain tokens to access Azure resources securely. This approach streamlines authentication and strengthens security by removing the need to manage sensitive credentials, while enabling conditional access and workload verification.
Aembit previously added support for both GCP Workload Identity Federation and AWS STS Workload Identity Federation. All three flavors of WIF can be configured and used by your application allowing dynamic application access across multiple clouds with minimal or no changes to code.
The Role of Managed Identities in Azure Entra ID
Managed identities in Azure Entra ID provide an automatically managed identity for applications to use when connecting to resources that support Azure Entra authentication. This eliminates the need for developers to manually manage credentials. There are two types of managed identities:
- System-assigned managed identities: Created and tied to a specific Azure resource, such as a virtual machine. The lifecycle of this identity is linked to the resource. If the resource is deleted, the identity is also deleted.
- User-assigned managed identities: Created as standalone Azure resources, these can be assigned to multiple Azure resources. Their lifecycle is independent, and they must be explicitly deleted when no longer needed.
These managed identities allow applications to authenticate to any service that supports Azure Entra authentication without the need for embedded credentials in the code.
Aembit Integration With Azure Entra Workload Identity Federation
With Aembit support for Azure Entra Workload Identity Federation, organizations can use Aembit as a third-party federated identity provider (IdP) to obtain credentials without added friction. This integration delivers several key benefits:
- Automatic credential acquisition: Applications can automatically obtain the necessary credentials through Aembit, simplifying the authentication process.
- Enhanced security: By federating identities, organizations eliminate the need to manage and rotate secrets – reducing the risk of credential exposure.
- Simplified access management: Aembit’s integration makes it easier to access Azure Entra–registered applications and managed identities, cutting down on complexity and overhead.
Benefits of Using Aembit With Azure Entra Workload Identity Federation
Integrating Aembit with Azure Entra Workload Identity Federation offers several advantages:
- Seamless multi-cloud integration: Organizations operating in multi-cloud environments can use Aembit to provide a unified identity solution, enabling consistent authentication across platforms.
- Improved security posture: By eliminating the need for applications to manage secrets, Aembit reduces the attack surface and lowers the risk of credential leakage. Aembit trust providers can verify the identity of the client workload, while conditional access support and integrations can assess client posture, geolocation, and more.
- Operational efficiency: Automatic credential management reduces the administrative burden of manual secret rotation and management, freeing teams to focus on core business functions.
How It Works
The integration process involves establishing a trust relationship between Aembit and Azure Entra ID. Here’s a high-level overview of the steps:
- Configure Aembit as an identity provider in Azure Entra ID: Set up Azure Entra ID to trust tokens issued by Aembit. This involves creating a federated identity credential in Azure Entra ID that specifies Aembit as the trusted IdP.
- Assign managed identities to applications: Depending on the application’s requirements, assign either system-assigned or user-assigned managed identities. This enables the application to request tokens from Azure Entra ID.
- Authenticate the application: When the application needs to access an Azure resource, it requests a token from Azure Entra ID. Azure Entra ID validates the token issued by Aembit and, upon successful validation, issues an access token for the requested resource.
This workflow ensures that applications can securely access Azure resources without handling sensitive credentials directly.
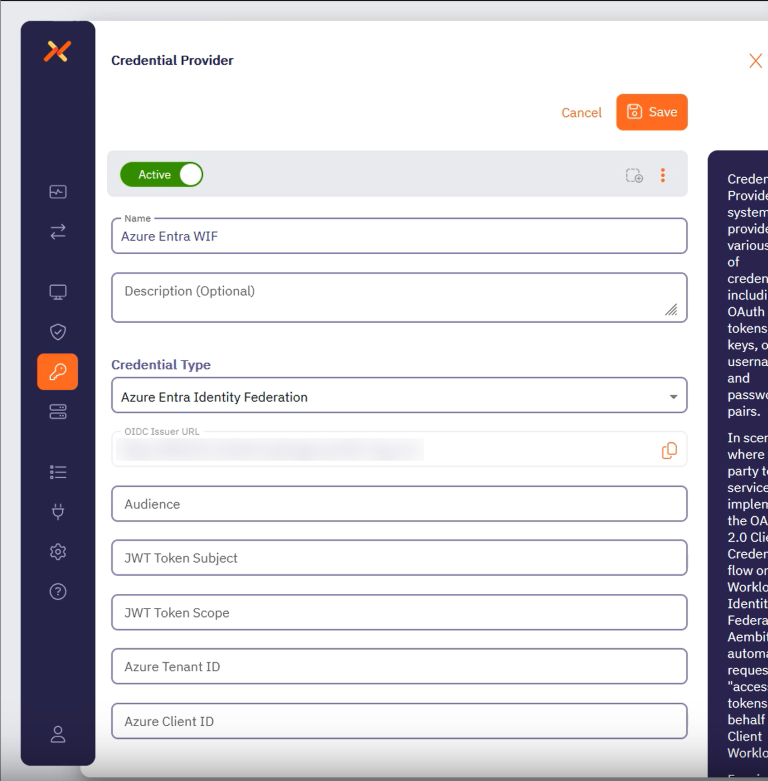
In the Aembit UI, adding Entra ID WIF as a credential provider is completed on a single screen:
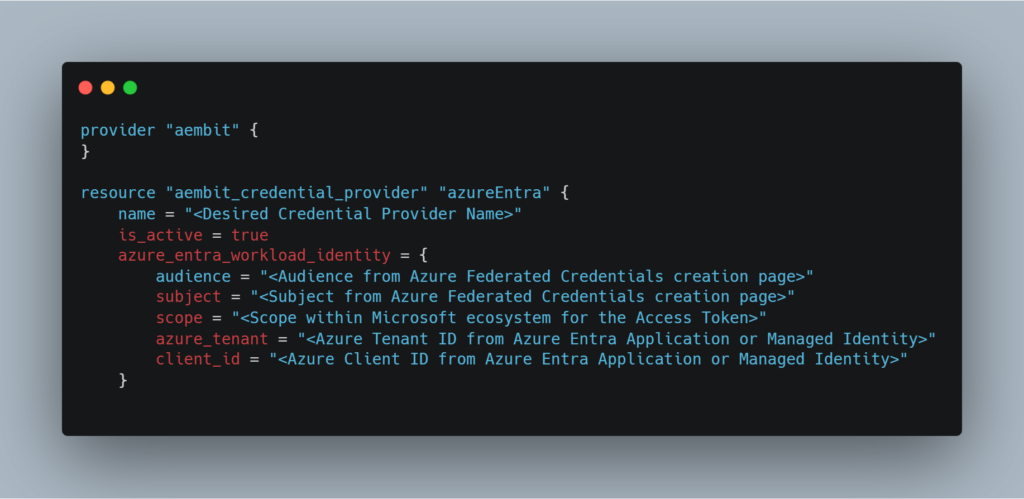
Configuring this credential provider using Aembit Terraform Provider is also available and using the following simple structure:
Getting Started With Aembit and Azure Entra WIF
To begin leveraging this integration, follow these steps:
- Review prerequisites: Ensure you have the necessary permissions in both Aembit and Azure Entra ID to configure identity federation.
- Set up Aembit as a federated IdP: In Azure Entra ID, configure a federated identity credential that recognizes Aembit as a trusted identity provider.
- Assign managed identities: Determine whether your application requires a system-assigned or user-assigned managed identity, and configure it accordingly in Azure.
- Update application code: Modify your application to take advantage of Azure Entra ID using the managed identity. This typically involves using Azure’s SDKs or API endpoints designed for this purpose. When APIs are used, no code is needed for authentication or credential retrieval or injection.
- Test the integration: Validate that your application can successfully authenticate and access the required Azure resources using the managed identity obtained through Aembit.
Conclusion
Aembit’s Azure Entra ID Workload Identity Federation support marks a significant advancement in secure and efficient authentication for Azure-dependent applications. By leveraging this integration, organizations can strengthen their security posture, reduce operational complexity, and enable seamless access to Azure resources. Aembit’s expanded set of credential providers allows your applications to use a growing number of services from a variety of vendors – without generating, storing, retrieving, or coding static, long-lived credentials.
For detailed guidance and step-by-step instructions, refer to Aembit’s official documentation on Azure Entra Workload Identity Federation.
The Workload IAM Company
Manage Access, Not Secrets
Boost Productivity, Slash DevSecOps Time
No-Code, Centralized Access Management




