GitHub Actions environment variables power the automation that builds, tests, and deploys your code. These variables connect your pipelines to external systems, databases, and cloud providers.
This makes environment variables a common entry point for attackers.
A 2024 report from Legit Security found that most GitHub Actions workflows have critical security flaws. Over 7,000 workflows interpolate untrusted input, more than 2,500 execute untrusted code, and 86% don’t limit token permissions.
These gaps leave your pipelines vulnerable to privilege escalation, credential leaks, and code injection.
Static secrets embedded in environment variables are often long-lived, over-permissioned, and hard to track. A leaked token in a public repo or a stale secret reused across workflows can open the door to attackers.
Tokens that show up in code or variables can accidentally be observed or written to logs, which further puts you at risk.
This security model deteriorates rapidly in cloud-native environments where containers, serverless functions, and ephemeral infrastructure demand nimble authentication.
Static secrets can’t keep up with dynamic workloads, and attackers know it.
Static secrets don’t scale with modern pipelines. To keep pace with dynamic workloads, authentication must evolve.
Why GitHub Actions Environment Variables Are Valuable – and Risky
GitHub Actions environment variables enable seamless integration within your CI/CD workflows by providing configuration settings and credentials locally to individual workflow steps, jobs, and even across separate workflows. They facilitate communication and coordination within the GitHub
Actions environment but do not extend beyond it to external servers or services in your broader infrastructure.
These variables often contain sensitive information such as API keys, tokens, and other secrets required to interact with cloud services or external APIs. Since workflows may run on GitHub-hosted runners or self-hosted runners, any exposed secret in these environments can provide attackers with a gateway into your systems, making the protection of these secrets critical.
What makes managing these environment variables tricky is their varied scope. Variables can be set at the workflow, job, or step level, and each scope affects how widely the sensitive data is exposed.
For example, a custom environment variable set at the workflow level is available throughout the entire workflow, while a variable set at a specific step is only accessible within that step:
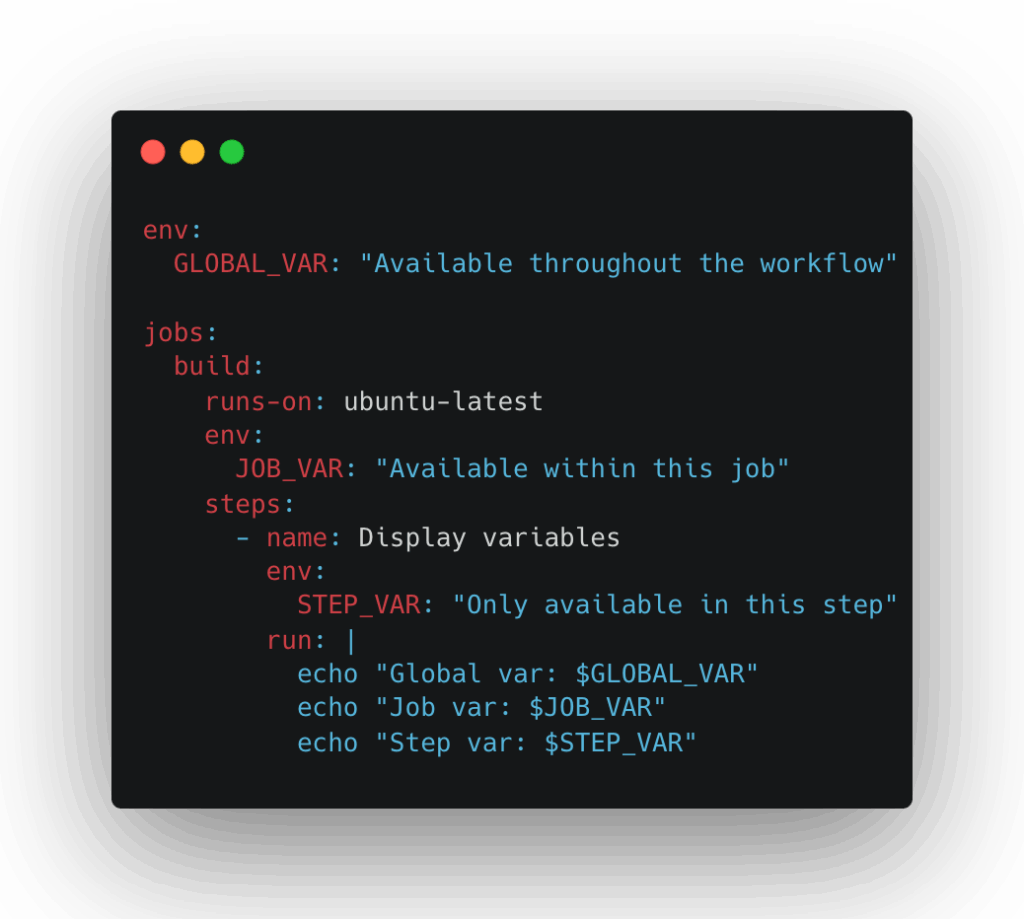
While this flexibility is powerful, it also means that without careful control, secrets and sensitive environment variables might be exposed to more steps or jobs than necessary, increasing risk.
Managing environment variables thoughtfully, with the principle of least privilege in mind, is essential to keep your workflows secure and efficient.
Understanding GitHub Actions Environment Variables and Secrets
In GitHub Actions, environment variables come in three primary types, each serving distinct roles within your workflows:
- Default environment variables: These are automatically provided by GitHub Actions for every workflow run. They include details like the repository name, the branch or tag that triggered the workflow (also known as the tag ref), and the repository owner. These variables give your workflows context about where and why they’re running. Note: These variables apply to the entire workflow, which is a set of actions that are executed in sequence.
- Custom environment variables: You define these explicitly in your workflow file using the env key declaration. They can be scoped at the workflow level, job level, or even limited to a particular workflow step, allowing precise control over where and when variables are available.
- Secrets: These are special variables used to store sensitive information such as API keys or passwords. GitHub keeps these encrypted in the secrets tab of your repository or organization. They are injected securely into your workflows at runtime but are never exposed in logs or the workflow file itself. Secrets are automatically redacted from logs to keep sensitive data secure.
Here’s an example demonstrating these scopes in action, including secure secret usage:
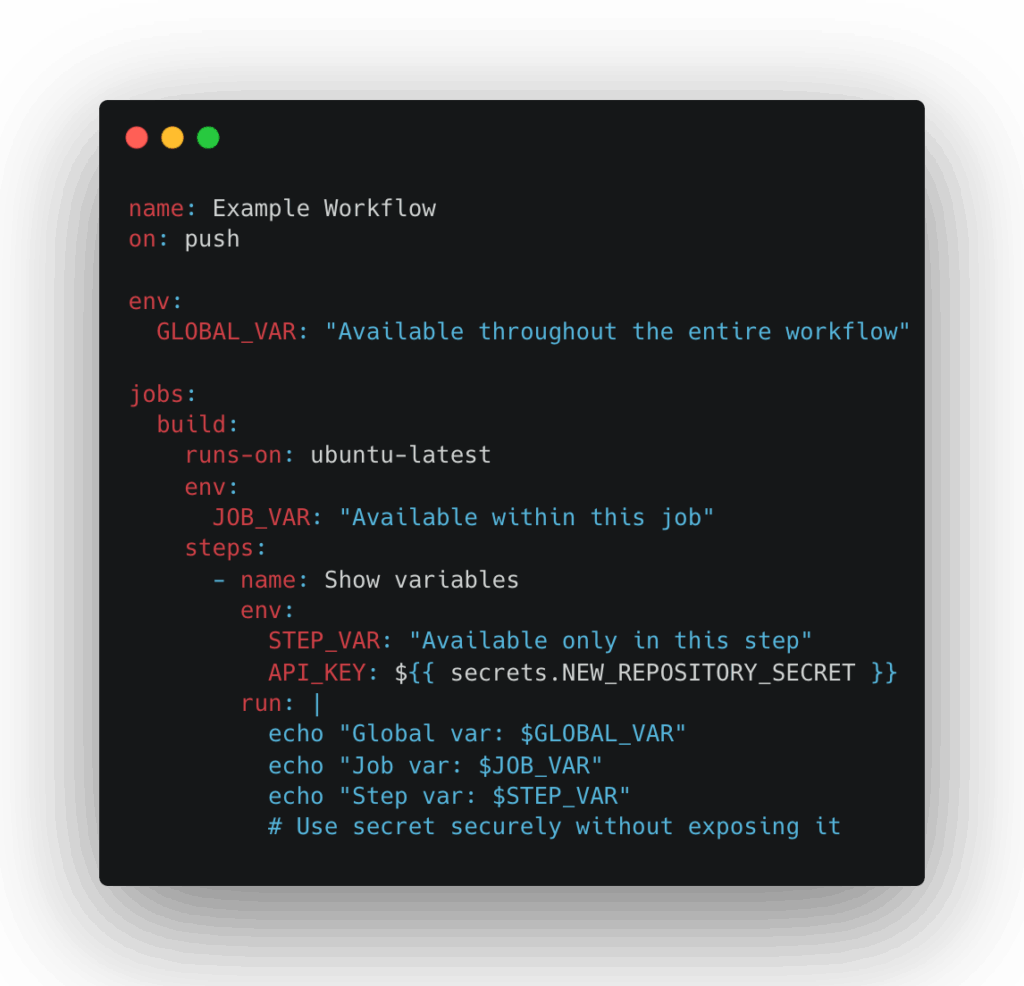
Variable Hierarchy in GitHub Actions
The scope of environment variables in GitHub Actions is hierarchical, and understanding how they propagate across actions, jobs, and workflows is key to managing access:
- Workflow-level variables are available across all jobs and steps in that workflow.
- Job-level variables apply only within a single job, limiting their scope to actions within that job.
- Step-level variables are the most limited in scope, available only within a specific step in the workflow.
This hierarchical structure allows for granular control over where each variable is accessible, reducing the exposure of sensitive data such as secrets.
The Limitations of Static Secrets in GitHub Workflows
Even with careful management of environment variables and adherence to best practices, static secrets can still be a prime vector for vulnerability. Long-lived repository secrets and persistent API keys create inherent operational friction and security vulnerabilities that modern development velocity exposes.
Operational Complexity of Managing Secrets
Managing secrets across multiple workflows and multiple jobs is operationally complex. GitHub allows up to 1,000 organization and 100 repository secrets per repository, but no centralized management view spans environments.
This fragmentation often leads to secrets being duplicated or copied between environments, such as the staging environment and the production environment.
This makes secret rotation manual and error-prone and increases the risk of stale or over-permissioned secrets.
Security Risks in Dynamic CI/CD Environments
Static secrets are brittle in the dynamic world of modern CI/CD. They are bound to workflow or job environment variables but without validating the job context or the identity of the running process.
As a result, a secret exposed in one workflow run can be reused or misused in another or even by compromised self-hosted runners. Furthermore, any user with write access to a GitHub repository can read all configured secrets, making least-privilege enforcement difficult and increasing accidental or malicious exposure risks.
In March 2025, the popular tj-actions/changed-files GitHub Action was compromised, exposing secrets, including API keys, tokens, and passwords, for over 23,000 repositories.
The malicious code scanned runner memory for secrets and printed them into build logs, exposing sensitive information to anyone with log access. This incident highlights how secrets injected as environment variables can be exfiltrated if a workflow or action is compromised.
Challenges in Auditing and Compliance
Auditing secret usage presents some significant visibility challenges. GitHub lacks comprehensive access logging for secrets, creating blind spots that prevent security teams from tracking which specific pipeline components accessed sensitive data.
Secret leakage into logs occurs through multiple vectors.
Developer debugging statements that print environment variables, command outputs containing credentials, and deliberate exfiltration attempts all bypass protection mechanisms. Even though GitHub implements log redaction, this protection only catches exact string matches of credentials in their original form. This still leaves transformed or partially-leaked secrets exposed.
Common Pitfalls in Secret Handling
A persistent problem is hardcoding secrets directly in workflow files or scripts, or passing them insecurely via command-line arguments. These practices risk revealing sensitive information through build logs or committing secrets to version control.
Static secrets are fragile, hard to maintain, and introduce significant risk. Recent high-profile breaches, such as the 2022 LastPass incident, where exposed credentials put millions of users at risk, highlight the vulnerabilities inherent in managing static secrets. These events reinforce the urgent need for new approaches like secretless workload identity to better secure GitHub Actions environments.
Why Traditional Secrets Management Falls Short
Even with GitHub’s encrypted secrets and scoped environment variables, most CI/CD workflows still rely on long-lived credentials—tokens, keys, and passwords that must be injected into runners at runtime.
This model creates several challenges:
- Secrets must be provisioned, rotated, and revoked across environments and workflows.
- Any developer with write access to the repository can access secrets—even if their job doesn’t require it.
- Secrets stored in memory or echoed into logs become low-hanging fruit for attackers.
Traditional key management systems (KMS) and secrets managers can help, but they don’t eliminate the secrets—they just move them around.
That’s why forward-looking teams are adopting secretless authentication: replacing stored secrets with ephemeral credentials tied to real-time workload identity. Rather than storing secrets in GitHub, the workflow authenticates itself when needed, and gets a tightly-scoped credential only for the current job.
This is the gap Aembit fills.
Future-Proofing Your GitHub Actions Workload Identity Security
Secret sprawl remains a significant challenge in CI/CD pipelines. Even with GitHub’s recommended practices, long-lived static secrets risk exposure, misuse, or being overlooked.
Workload identity security offers a modern alternative by replacing static credentials with real-time, short-lived access tokens. This means your GitHub workflows request access only when needed, without storing secrets in memory or environment variables.
- No more hardcoded secrets in workflows
- No ambiguity about which workload accessed resources and when
- No fragile credential rotation processes across development, staging, and production environments
By validating each workflow job’s identity and policy before issuing ephemeral credentials, this approach eliminates the need to distribute or store sensitive secrets across repositories or runners.
Adopt a modern, secretless identity security model for your CI/CD workflows—without disrupting your existing processes.
Visit us at Aembit.io to learn more or request a demo.
The Workload IAM Company
Manage Access, Not Secrets
Boost Productivity, Slash DevSecOps Time
No-Code, Centralized Access Management