In a previous post, we provided a step-by-step approach to implement OAuth 2.0 for secure access to BigQuery, Google’s fully managed, serverless data warehouse, which has become an indispensable tool for businesses seeking to analyze large datasets at rapid speed.
Today, we are going to share how to implement the Aembit Workload IAM Platform for secure access to BigQuery. Aembit makes the process easier by automating the integration of BigQuery with identity-based access control, utilizing Google Workload Identity Federation.
This method ensures a secure, seamless connection to BigQuery by leveraging Aembit’s dynamic credential management and conditional access policies, aligning with the security and compliance frameworks essential for handling sensitive data in cloud environments.
Let’s get started!
Prerequisites:
This example assumes that you have a GCP project with BigQuery enabled and data to query, and an Aembit tenant with the Aembit Edge deployed.
Steps:
1. Log into GCP and go to the ‘IAM & Admin -> Service Accounts’ section. This can be accessed directly by going to https://console.cloud.google.com/iam-admin/serviceaccounts
a. Make sure you are in a GCP project which you are authorized to use, for this example, we’re using ‘My Project 84846.’
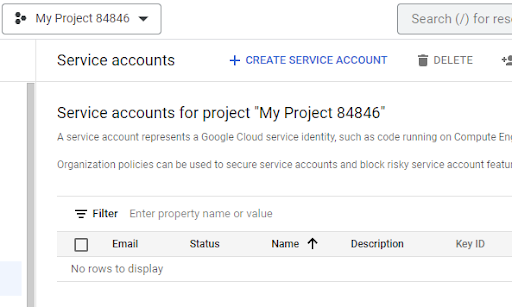
b. Click the ‘Create Service Account’ button and specify a name (e.g. BigQuery Demo), customize the ID (optional), and add a description. Then click ‘Done.’
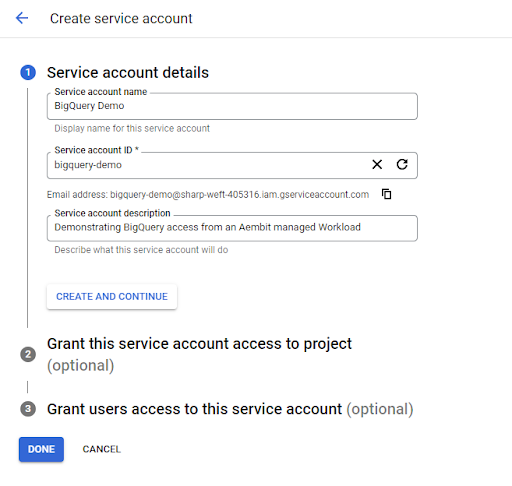
[If you’d like, additional conditions and limitations can be added to the service account, but are outside the scope of this article.
2) Log into the Aembit platform and go to ‘Credential Providers’ and click the ‘New’ button.
a. Add a credential provider by entering a name and description (optional), and then selecting the ‘Google Workload Identity Federation Credential Type.’
b. Paste in the service account email address from Step #1.
c. If you’d prefer, you can set a custom ‘Audience’ here, but for this demonstration, we’ll come back to the ‘Audience’ after step No. 3 below.
3) Log into GCP and go to the ‘IAM & Admin -> Workload Identity Pools’ section. This can be accessed directly by going to: https://console.cloud.google.com/iam-admin/workload-identity-pools
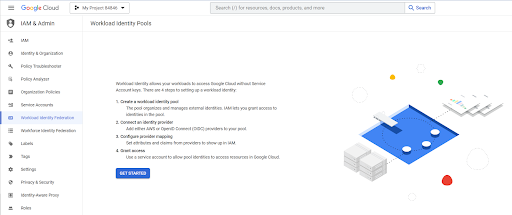
4) Click on the ‘Get Started’ button to create a GCP workload Identity Federation with your Aembit tenant.
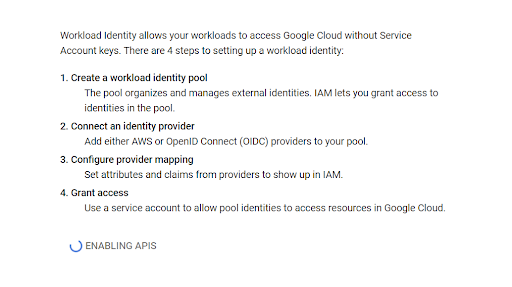
a. Begin the process by providing an ‘Identity Pool Name’ and description (optional), then click ‘Continue.’
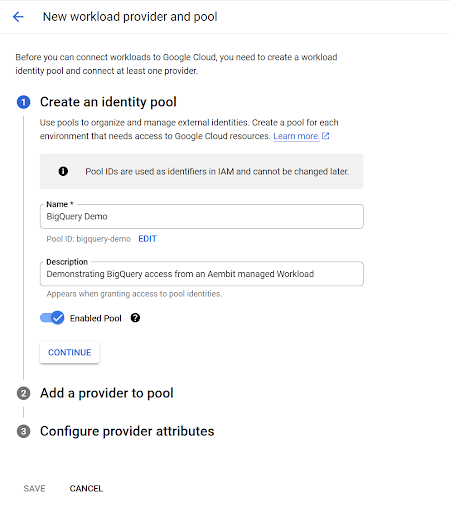
b. Now, select the provider type as ‘OpenID Connect (OIDC),’ specify a provider name, and the OIDC issuer URL from the Aembit credential provider you created in step No. 3. Leave the ‘Audiences’ option set to ‘Default’ audience and click ‘Continue.’
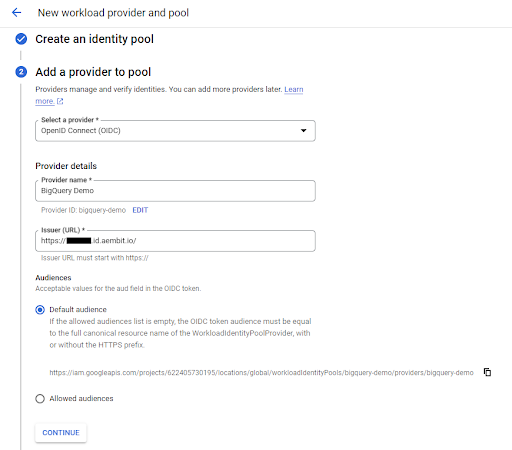
c. Lastly, specify the provider attribute of assertion.tenant in OIDC 1 and click ‘Save.’
5) Now, let’s grant access from the GCP Workload Identity Federation to the GCP Service Account we created in step No. 2.
a) Within the GCP workload identity pool we just created, click on ‘Grant Access.’
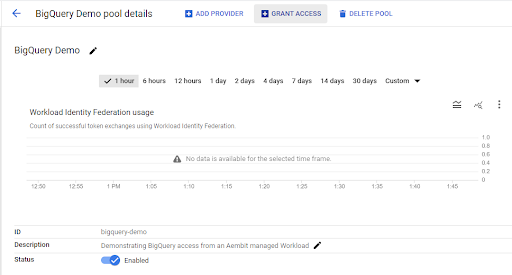
6) Back in Aembit, on the ‘Credential Provider,’ enter the default audience for your GCP workload identity federation pool and click ‘Save.’
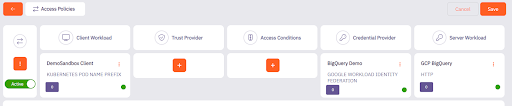
7) Continuing in Aembit, create and configure an access policy that uses the client workload, credential provider, and server workload we’ve created.
8) Now we can verify connectivity.
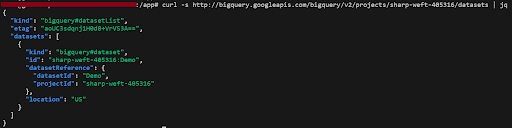
a) For this demonstration, we’ll use curl from the command line of the Kubernetes Pod which we configured as the client workload and we see that we can successfully retrieve the set of BigQuery data sets available.
Experience the Difference with Aembit
As you consider transitioning from traditional methods to the Aembit Workload IAM Platform for securing access to Google BigQuery, keep in mind the fluidity it will bring to your team. Aembit not only simplifies the authentication process but also provides a more consistent, resilient, and integrated experience, making your data management tasks less cumbersome and more efficient across environments.
Discover how Aembit can transform your experience. Try us for free at aembit.io.
The Workload IAM Company
Manage Access, Not Secrets
Boost Productivity, Slash DevSecOps Time
No-Code, Centralized Access Management



