Aembit now allows you to secure HashiCorp Vault, while reducing its operational burden on developers and DevOps teams. This capability is generally available today, and is also available in our self-service free tier that supports up to 10 production-class workloads.
With this new capability, you can now secure your Vault by providing policy-based access from workloads based on cryptographically verifiable identities instead of bootstrap secrets, paired with the ability to implement conditional access based on the workload’s security posture. You can enable this across all of your cloud and on-prem environments, without making code changes to your applications.
Secrets Managers are Essential to Modern Applications
Secrets managers (sometimes referred to generically as vaults) are essential in modern applications because they serve as the guardians of sensitive data, safeguarding critical secrets, certificates, and encryption keys. Secrets managers have grown from being just a secure repository for these secrets to attempting to add robust access controls and automation for secret lifecycle management. Whether it’s protecting API keys, database credentials, or cryptographic assets, Vaults are the “password managers” of machine-to-machine access, helping businesses safeguard the integrity and confidentiality of data in their most sensitive applications.
Using HashiCorp Vault for secrets management can bring significant benefits to an organization, but it also comes with its share of burdens that impact both the DevOps teams managing it and the developers who are integrating it into their applications. So – just like user access evolved – we think machine to machine access is ready for IAM as well.
When working with our customers, we saw some common challenges, such as the “secret zero” problem, access control, policy management, token management, dynamic secrets, and logging.
Our goal with this new capability is to allow customers to take full advantage of their Vault investment with lower friction and operational overhead.
Securing Vault with Workload IAM
If you’re just learning about Workload IAM, this technology enables your workloads to access sensitive data and applications based on their identity and posture, combined with an access policy versus simply by having a secret.
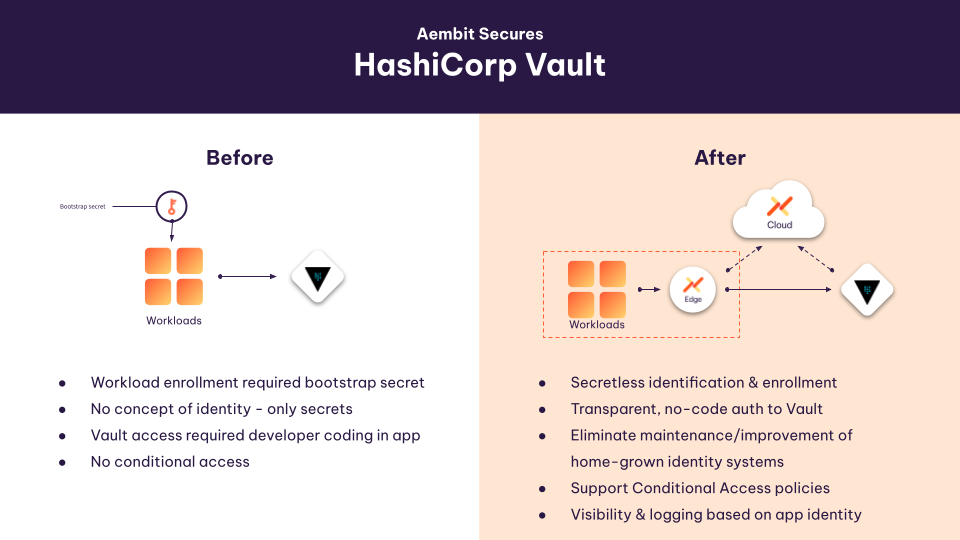
This is a simple and powerful approach to securing Vault access, or access to any sensitive data or application in your environment. Deploying Aembit gives your team a few advantages:
- Define identity-based access policies to control access to Vault
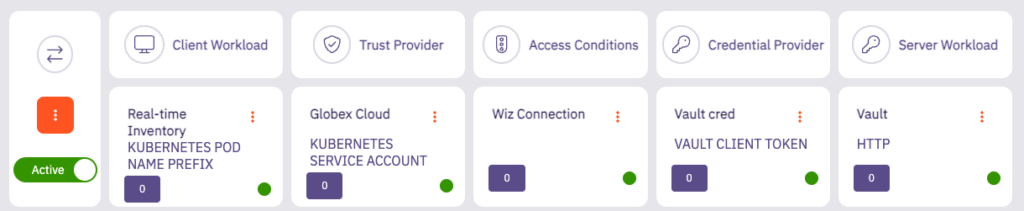
Vault contains sensitive information, and the proverbial ‘keys to your kingdom.’ Aembit gives your DevOps and security teams a central, policy-based method to control which applications have access to your Vault, based on their cryptographically validated identities. (For more on this, see ‘How Aembit Works’). Easily visualized in our UI, it also enables your teams to leverage policy as code to add or block Vault access as needed.
- Eliminate the secret zero problem
- Eliminate complex Vault integration
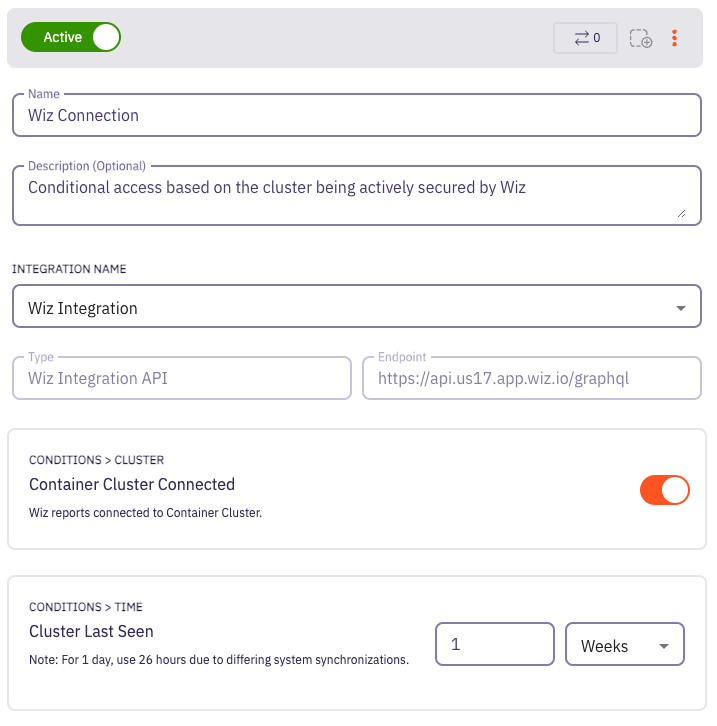
- Implement conditional access to Vault
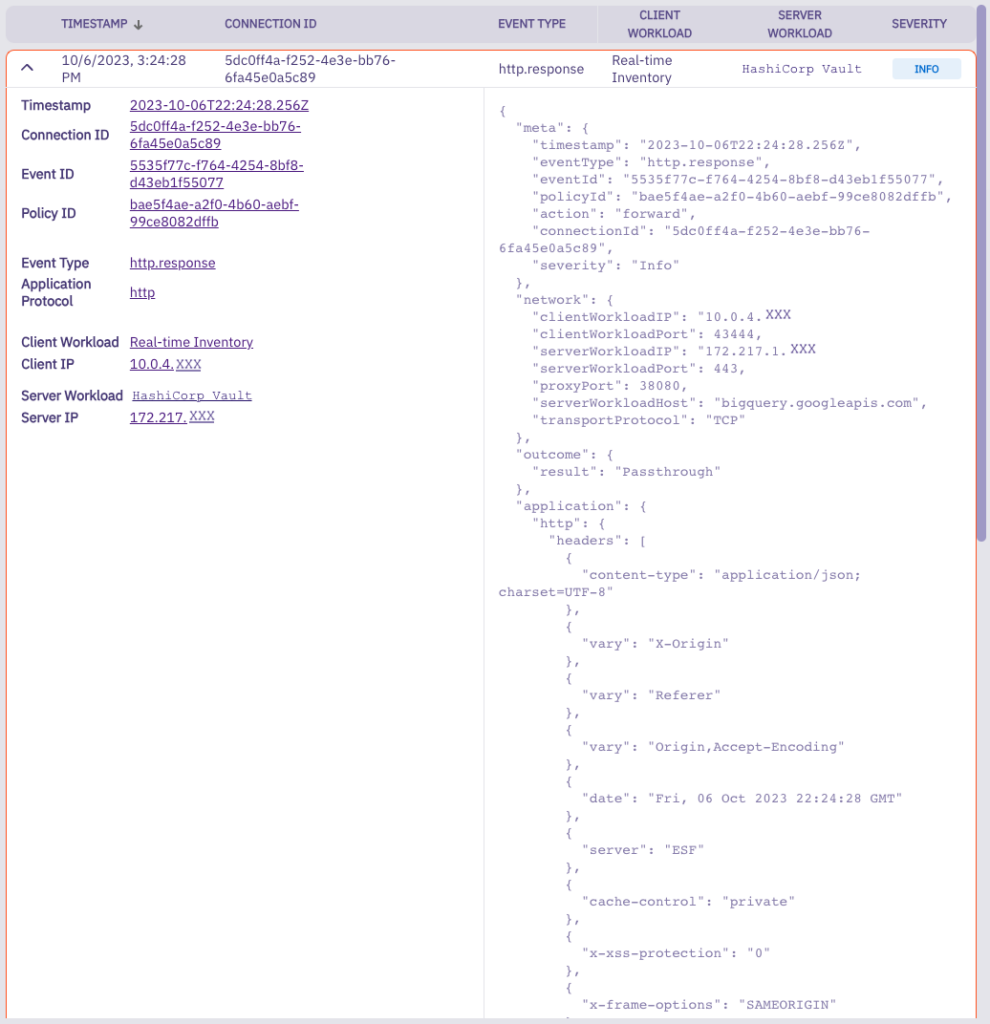
- Provide centralized visibility, logging, and audit of your Vault access – based on identity instead of secrets.
Protect HashiCorp Vault Today, Everything Else Tomorrow
Aembit’s model is to provide you a centralized workload identity provider that can offer IAM between all of your critical applications. You can start by securing access to HashiCorp Vault today, and then easily extend the same model across all of your sensitive databases, applications, SaaS Services, and even third-party APIs in the future.
Along the way, you can reduce friction for your DevOps teams who need to manage these connections and lift a burden from developers who otherwise have to program strong, sophisticated auth when they instead could be focused on features that drive your own product forward.
Get Started Today: Free and on Your Own
The Aembit free tier is designed to provide highly reliable, highly performant Workload IAM to you today. It’s designed to be self-service, so you can get started whenever the inspiration strikes. We’re, of course, happy to help you on your journey. Whatever you choose, get started on improving your HashiCorp Vault experience today.



