Like Google Cloud before it, Aembit now supports AWS workload identity federation (WIF), extending its universal identity federation capabilities. This integration enhances non-human access security, improves the developer experience, and simplifies multi-cloud and on-premises federation.
AWS Security Token Service (STS) WIF issues short-lived tokens for AWS access, but the Aembit Workload IAM Platform eliminates the need for managing secrets or modifying developer code for authentication. By cryptographically identifying client workloads, Aembit adds an extra layer of security with MFA and conditional access – even when the service itself doesn’t natively support those capabilities.
Why Use WIF and Aembit
Before configuring WIF, here’s why pairing it with Aembit strengthens security and simplifies management:
- Secure Multi-Cloud Access: Applications outside AWS can securely connect to AWS resources without managing service account keys, reducing credential leakage risks. Aembit injects tokens dynamically, requiring no code changes.
- Unified Federation Across Environments: Hybrid and multi-cloud organizations can consolidate workload identity management with a single identity source. Aembit supports deployments across on-prem, SaaS, cloud, and serverless environments.
- Seamless Cloud Migration: Existing applications retain their identities during cloud migrations without re-architecting authentication. Aembit’s policies enable a smooth transition without modifying the application or identity provider.
- Temporary and Ephemeral Access: WIF issues short-lived tokens for enhanced security. Aembit enforces conditional access policies, restricting access by origin, time, and risk level – ensuring one-time access is both controlled and secure.
Pairing WIF With Aembit
An organization using AI tools to analyze sales data stored across Salesforce, Stripe, and AWS S3 can use Aembit’s AWS WIF support to simplify access. For a custom application storing transaction data in an S3 bucket, Aembit directs AWS STS to grant time-limited access without requiring long-lived secrets or hardcoded credentials. When pulling customer data from external sources like Stripe and Salesforce, Aembit enforces secure identity mapping and policy controls, ensuring integration through AWS STS-assumed roles.
Once the data is consolidated in S3, the application can use SageMaker for analysis, with Aembit managing secure identity federation to ensure access is granted only to necessary roles. This approach strengthens security, automates policy-driven authentication, and minimizes the complexity of managing sensitive data workflows—without requiring developers to write authentication or authorization code.
How Aembit’s AWS WIF Support Works
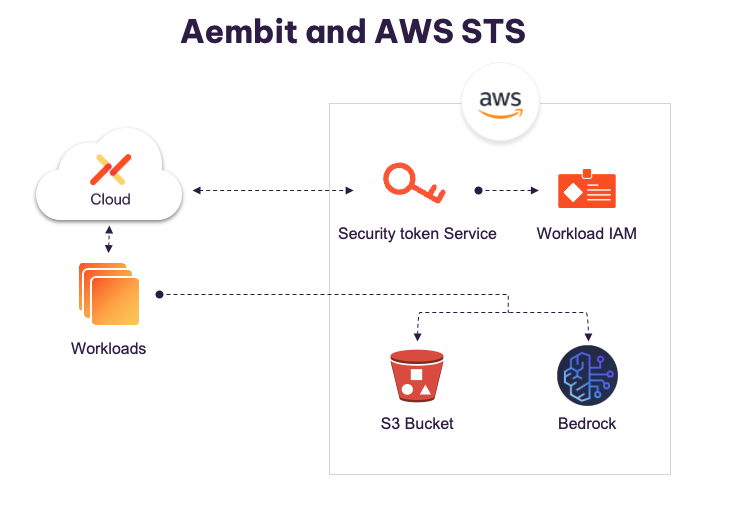
The diagram below illustrates how Aembit integrates with AWS STS WIF. On the AWS side, STS is enabled, and an IAM role is created with the necessary permissions for the target service.
Instead of using a service account directly, Aembit verifies that the workload is authorized to access the resource and requests a short-lived token from AWS STS. This token is linked to the IAM role and grants temporary access. Aembit then injects the token into the workload’s API call, allowing it to communicate with the AWS resource without storing long-lived credentials.
How AWS STS WIF Is Configured in Aembit
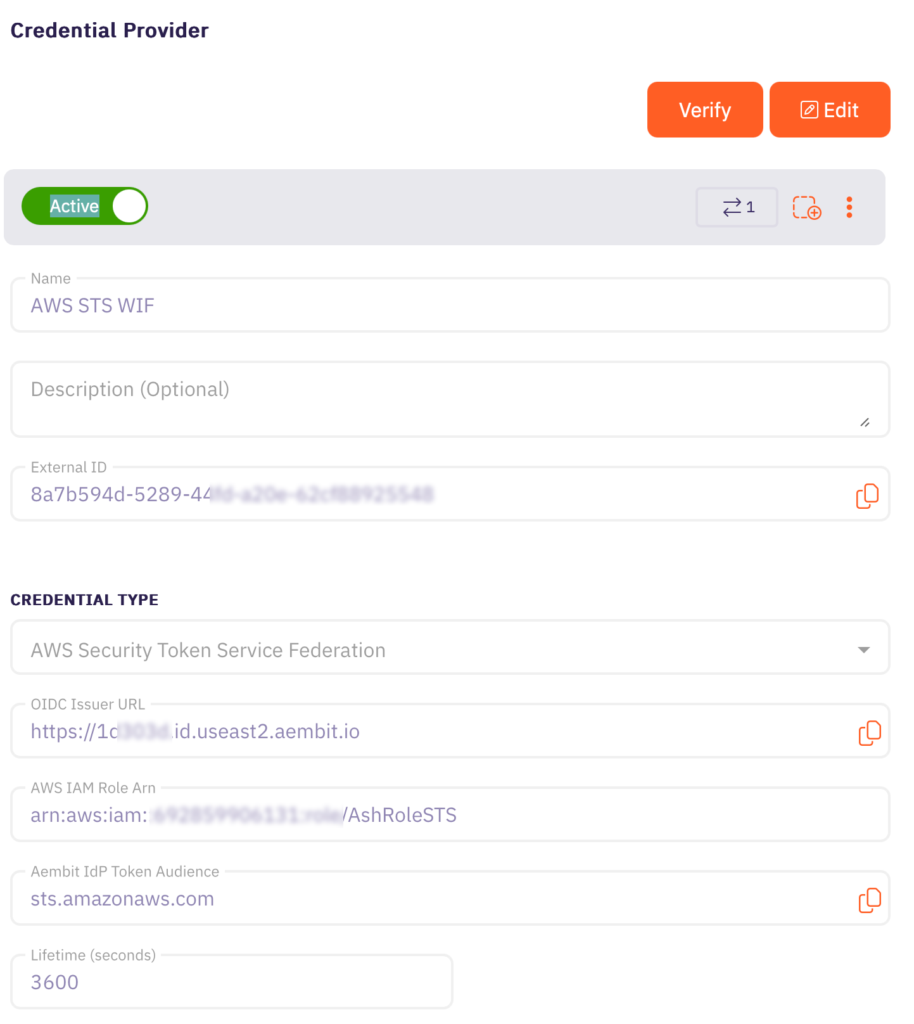
Below is the credential provider (CP) configuration for AWS STS. There are no hardcoded credentials or API tokens – static keys are avoided in favor of stronger authentication methods. OIDC is used to establish a trusted connection without storing secrets, reducing risk while maintaining compatibility with AWS security best practices.
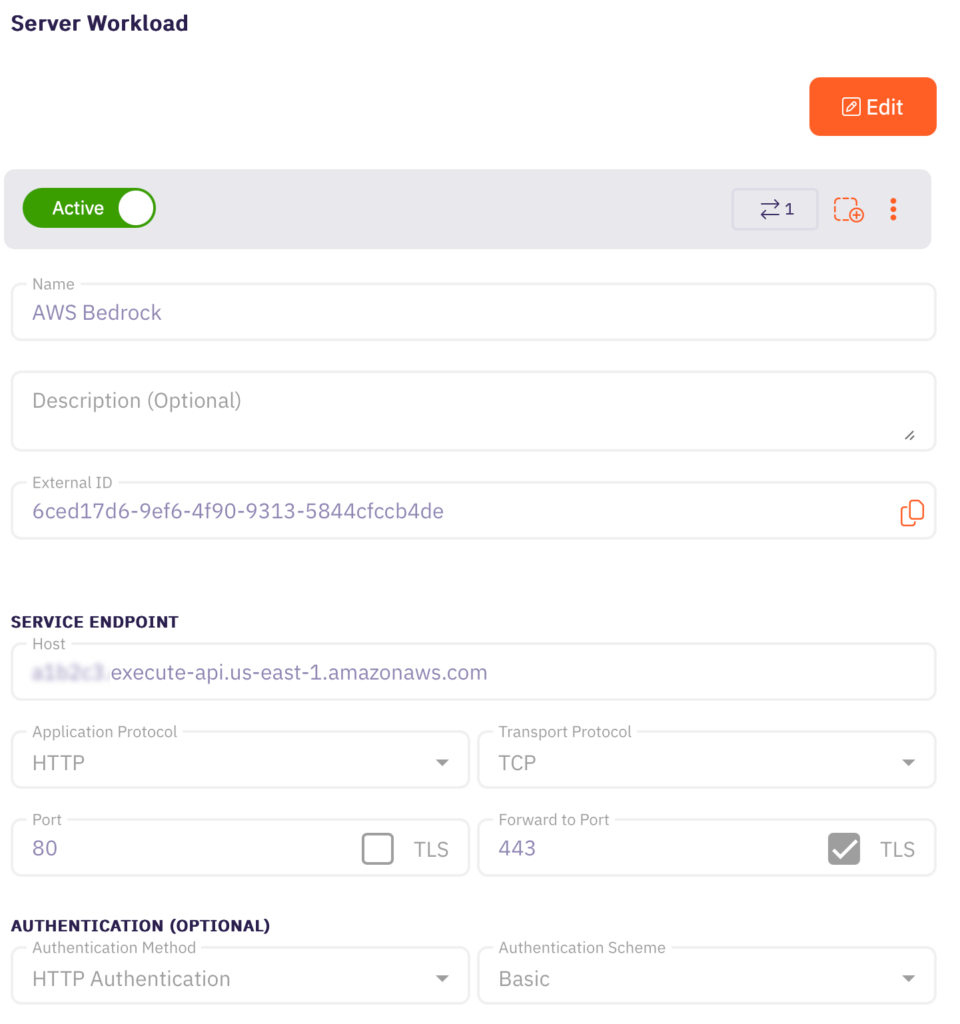
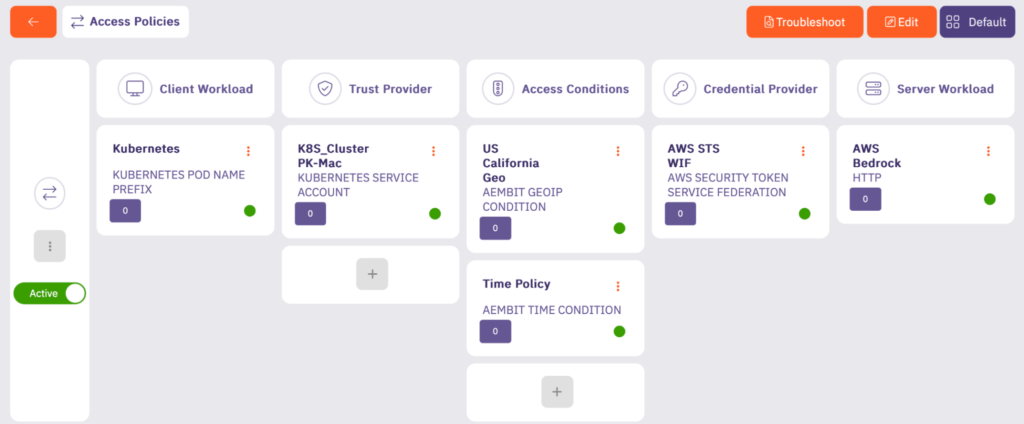
The access policy below defines the client workload – an application running in Kubernetes – by its pod name prefix. This workload is granted access only to AWS Bedrock, with no permissions for other AWS services.
The configuration also includes a trust provider that verifies the workload’s identity using a Kubernetes service account. To further restrict access, two conditions are applied: connections must originate from California, and requests can only be made within a specific day and time window for this application.
Request Code
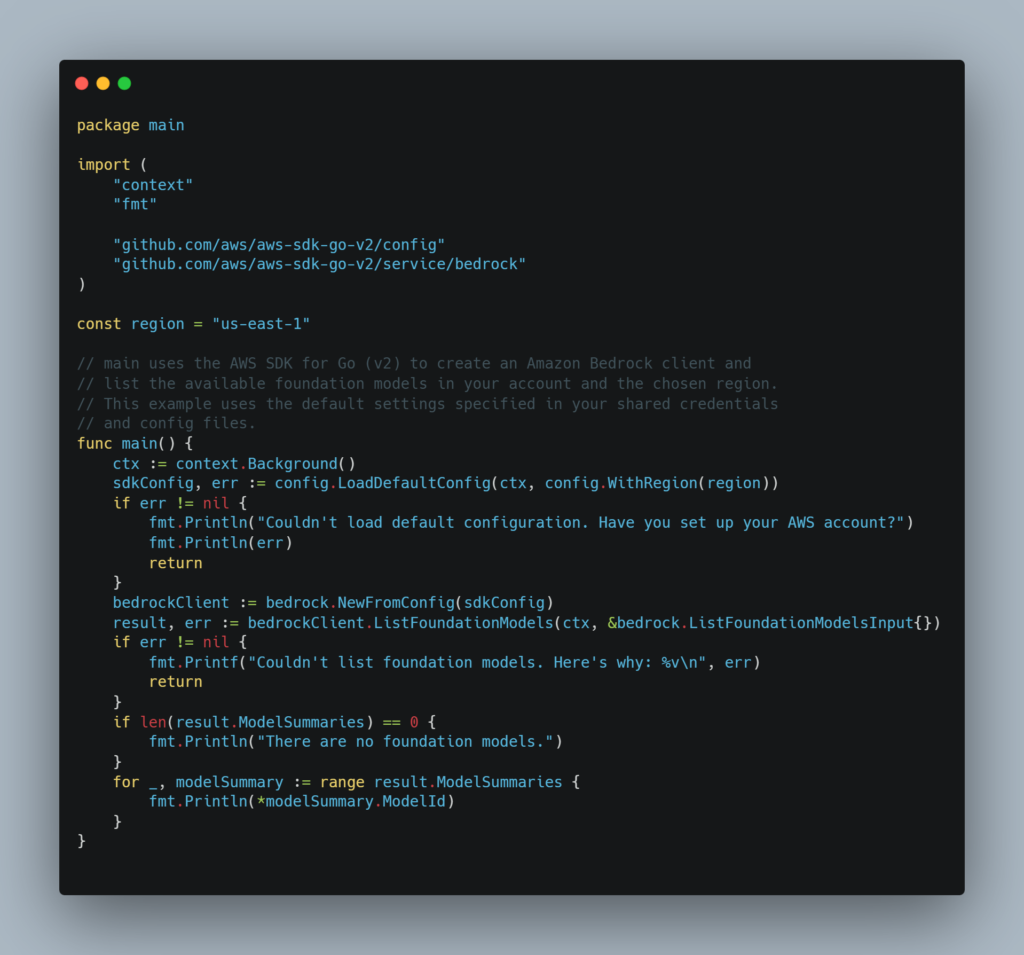
Here is some sample code for making basic Bedrock calls using the SDK (source).
To learn more about how Aembit’s WIF support can help secure and accelerate your Workload IAM deployment, schedule a demo today.
The Workload IAM Company
Manage Access, Not Secrets
Boost Productivity, Slash DevSecOps Time
No-Code, Centralized Access Management