Aembit enhances security and streamlines access for GitLab and other CI/CD platforms by leveraging identity federation and policy enforcement to replace long-lived secrets with dynamic, short-lived, just-in-time credentials.
This approach ensures that only cryptographically verified non-human identities can access sensitive data and resources.
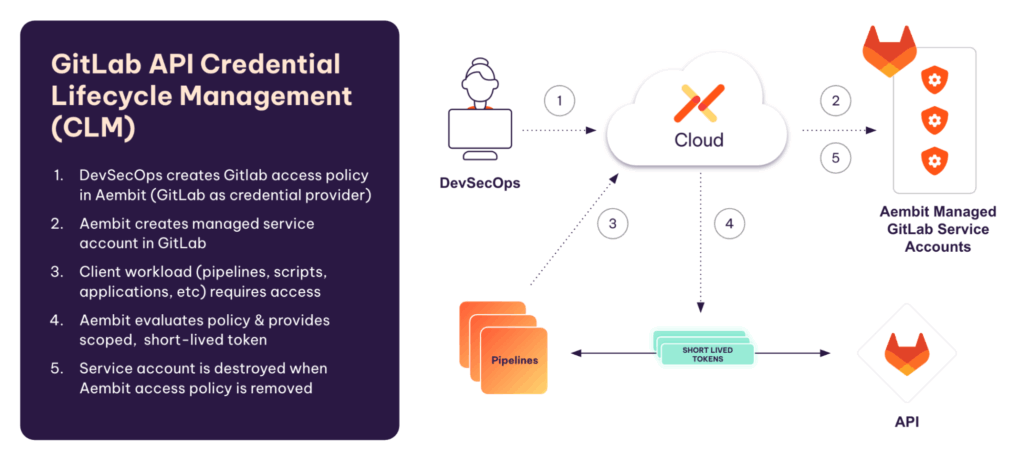
With our newest capability, personal access tokens (PATs) are dynamically injected upon request based on policy, and the related GitLab service account is created and destroyed only as it is needed. This automates the management of credentials, limits your blast radius with short-lived tokens, and prevents zombie service accounts.
Aembit’s latest innovation, Workload Credential Lifecycle Management, is part of our expanding suite of enhancements for GitLab and other CI/CD platforms.
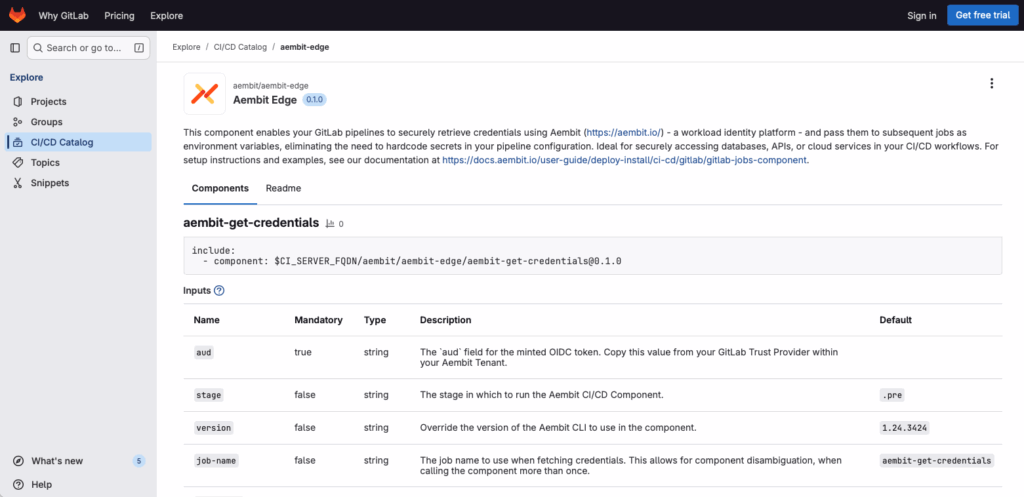
We are also happy to announce our GitLab Component, which can be found in Gitlab’s CI/CD Catalog. This component makes integrating Aembit with GitLab even easier and ensures that you’re always using the latest Aembit Edge.
The component enables your GitLab pipelines to securely retrieve credentials using Aembit and pass them to subsequent jobs as environment variables, eliminating the need to hardcode secrets in your pipeline configuration. The Aembit Edge agent is still supported for customers that have already deployed it in their Gitlab pipelines.
As organizations heavily rely on these platforms, DevOps, developers, and security teams are left to deal with the complexity of managing access between CI/CD tools and other sensitive data in the organization. Security teams must prevent breaches, while DevOps and developers are trying to ensure that systems and applications still work consistently without too much overhead.
Recent incidents show how exposed tokens and excessive access rights translate these challenges into real exposure risks.
For example, the January 2025 breach of Pearson and a repeat compromise of the Internet Archive were due to exposed GitLab tokens and over privileged accounts, leading to terabytes of stolen data, potential lateral movement, and risks of lost IP and customer trust.
Here is how Aembit secures and automates the credentials in your GitLab environment:
- Automated, policy-based access from Gitlab components. Aembit replaces the static, over-provisioned access rights that teams typically configure for CI/CD. Instead, Aembit automates the process of providing least-privilege, just-in-time access based on Identity, a policy, and short-term credentials.
- Support for GitLab SaaS and on-premises, self-hosted deployments. Aembit provides support for both GitLab.com and self-hosted, on-premises instances, offering flexible identity and access management that works across hybrid infrastructure.
- Granularly identify and attest each identity per pipeline, job, and runner. Aembit’s platform identifies individual GitLab jobs and runners with precision. It uses the token project path, ref type (branch or tag), and the specific ref (branch or tag name) to identify jobs. The GitLab trust provider feature attests to the cryptographic identity of client workloads running in a GitLab Jobs environment, verifying their identity before authorizing access and issuing credentials.
- Enforce Zero Trust conditional access for GitLab calls. Aembit enables Zero Trust conditional access policies for GitLab by evaluating requests based on verified identity and real-time conditions such as time of day and geography. This ensures that only authorized non-human identities can access resources, adhering to the principle of least privilege.
- Inject credentials just-In-time & remove locally stored credentials. Aembit eliminates the need for developers to store long-lived credentials locally or in a vault, eliminating work and preventing leaks. Aembit brokers access, handling credential management on behalf of the client workload, which allows you to safely remove any previously stored secrets.Aembit injects short-lived credentials into API calls only when needed, while eliminating the need for developers to code credential management.
- Automatically manage GitLab service accounts. Aembit can create and destroy service accounts so that they are only available when they are needed, automatically rotating credentials while the accounts are in use.. This reduces management overhead while minimizing another dimension of the attack surface.
- Additional features and enhancements. Aembit’s integration with GitLab also provides centralized access management for all workloads, and auditable access logs for all access events. Aembit also provides APIs and a Terraform provider to configure and manage Aembit programmatically.
All together, Aembit automates the enforcement of least privilege access rights in GitLab and enhances its security, while eliminating the ongoing management burden of credential rotation, service account management, and audit reviews.
GitLab: Your Software Assembly Line
CI/CD (continuous integration/continuous delivery) platforms are the backbone of modern software development, automating the entire process from code commit to production deployment.
These platforms streamline application delivery by managing a series of automated steps, starting with the developer committing code. The CI/CD platform then automatically kicks off a workflow, which involves integrating with various tools to ensure code quality and security. For instance, SonarCloud, Codacy, or Code Climate can be used for static code analysis and Codecov, Coveralls, or SonarQube for measuring test coverage. At the same time, the platform can use tools like Terraform Cloud and EC2 Image Builder to automate the provisioning and configuration of cloud environments, ensuring consistent and reproducible infrastructure.
Throughout this pipeline, CI/CD platforms manage several critical functions to maintain a secure and reliable delivery process. They ensure artifact integrity by digitally signing built packages, which guarantees that they have not been tampered with. The platforms also automate the deployment of test environments, where a suite of continuous regression tests can be run using tools like Qase, TestRail, or BrowserStack. Once testing is complete and the code is ready for deployment, the platform can automatically publish updated documentation. All of these automated tasks require a robust system for authentication and access control, ensuring that each step has the necessary permissions to interact with other applications and services. Furthermore, all actions within the pipeline are centrally logged and audited, which is crucial for security, compliance, and troubleshooting.
Ensuring that your “software assembly line” is secure and can be managed easily means enforcing least privilege, just-in-time access across every CI/CD touchpoint. . And organizations that run CI/CD at scale rely on being able to programmatically handle everything from initial account creation all the way to the decommissioning of policies as the “assembly line” evolves.
Shortcomings and Limits of Native Features
GitLab CI/CD is a secure platform, but even the best tools struggle to make access to other tools and access across trust domains secure and automated. For example, GitLab provides built-in mechanisms for managing variables and secrets, but these fall short for enterprise-grade security and scale.
- Static Secrets Proliferation: Teams often resort to storing long-lived API keys and personal access tokens as masked CI/CD variables, which are still static and vulnerable to leakage if the GitLab environment is compromised.
- Manual Credential Management: Manual rotation of secrets is error-prone, time-consuming, and frequently neglected, leaving systems exposed.
- Lack of Granular Control: Native GitLab variables offer limited granular access control, making it hard to enforce least privilege for individual jobs or stages.
- Fragmented Secret Storage: Secrets are scattered across GitLab variables, developer machines, and various external vaults, leading to inconsistencies and a lack of a single source of truth.
- Limited Auditability: Tracing who (or what workload) accessed which secret, when, and why is challenging, hindering compliance and incident response.
- Complexity of Federation: Implementing secure workload identity federation for cloud providers (AWS, Azure, GCP) or SaaS services directly within GitLab CI/CD requires significant boilerplate code and expertise.
What Aembit Workload IAM Provides
Previously we discussed how Aembit enables secretless, federated CI/CD pipelines. Customers love our ability to automate just-in-time credentials based on real time policy enforcement, and then have auditable logs that capture every access attempt.
Our customers wanted to extend this capability into personal access tokens, and their related service accounts.
Comprehensive Credential Lifecycle Management for GitLab
Aembit now manages the entire lifecycle of workload credentials for you. By integrating a managed GitLab account credential provider, we are not just providing a feature but are fundamentally transforming how machine identities and secrets are handled in your CI/CD pipelines.
This feature is built on a foundation of core capabilities that empower organizations to eliminate secret sprawl and strengthen their security posture. Once the short-lived token is issued, it is automatically injected into the pipeline, making it invisible to developers. This prevents accidental leakage and reuse. After the job completes, the credential is automatically revoked. This end-to-end process is fully managed by Aembit.
How the GitLab Service Account Integration Works
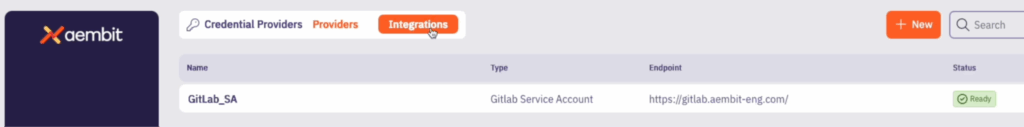
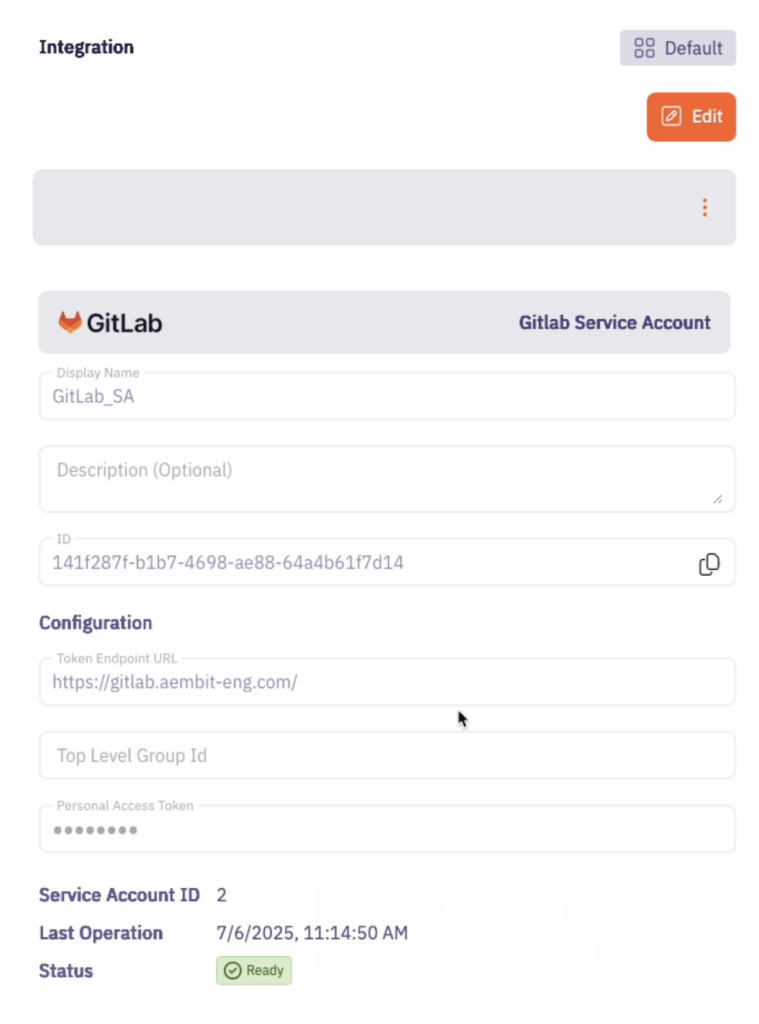
This GitLab service account integration uses a GitLab service account to connect with your GitLab instance and control credential lifecycle management for each managed GitLab account credential provider.
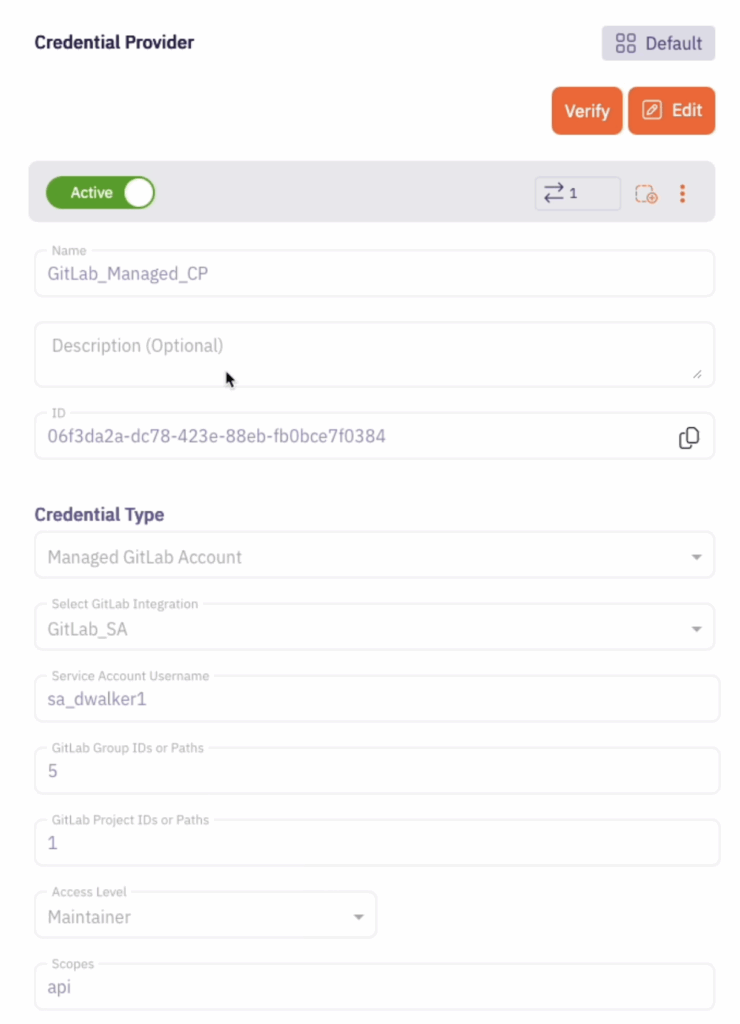
Once the integration is configured, new managed GitLab account credential providers are created which are scoped to only access specific GitLab projects or GitLab groups. Each provider creates an additional, separate GitLab service account that manages credentials on your behalf. This approach gives you fine-grained control over your GitLab workloads’ credential lifecycle management, as well as, fine-grained logging and auditing capabilities on both Aembit and your GitLab instance.
Configuring Credential Provider Integration for GitLab Service Accounts
The integration requires a service account with administrator permissions and a personal access token, which gets automatically rotated as soon as it is entered in the UI.
Once the integration is configured, multiple, limited scope credential providers can be configured to be used with each server workload. Each granular credential provider should be limited by GitLab group IDs or path, GitLab project ID or paths, one of the eight GitLab access levels, and a GitLab scope.
This announcement marks a major step forward for GitLab security and streamlined workflows.
By introducing GitLab Credential Lifecycle Management and the new GitLab Edge Component, we’re helping organizations move beyond the risks of static, long-lived credentials. These features fundamentally transform how your teams manage non-human identities, enabling you to automate the creation and destruction of credentials and service accounts based on dynamic, least-privilege policies.
The result? You significantly reduce your attack surface, eliminate manual overhead, and gain a clear, auditable trail of all access events. In a world where CI/CD pipelines are the backbone of modern software delivery, Aembit provides the essential layer of security and automation that ensures your software assembly line is not just efficient, but also secure by design.
Sign up for the ‘Starter Tier’ here and protect your GitLab in minutes.