We’re excited to announce Aembit Edge Discovery, a powerful new capability designed to bring actionable visibility to your distributed workloads.
Edge Discovery delivers precisely that – a dynamic, agent-based approach to mapping your workload ecosystem specifically for the purpose of bringing them under management with IAM policies.
Building on a Foundation of Comprehensive Discovery
Aembit Edge Discovery is a significant enhancement to our existing discovery capabilities.
While our integration with partners like Wiz provides invaluable insights into your cloud environments by pulling workload data directly from Wiz, Edge Discovery provides a deeper, agent-based view into the runtime behavior and intricate connections within your workloads, regardless of their environment.
This combination of cloud-native and agent-based discovery offers a holistic understanding of your distributed workload infrastructure. And this is just the beginning. Look forward to even more diverse discovery sources in future releases, ensuring Aembit provides the most complete picture of your non-human identities.
Growing Challenges of Workload Visibility
Applications and services are constantly interacting, creating an ever-expanding attack surface. Legacy methods of cataloging and managing these workloads, such as developer “best-effort registration” or using IGA tools, often fall short, leaving security gaps and operational blind spots. We’ve heard from countless organizations about the challenges of:
- Manual Overhead: Relying on manual processes, spreadsheets, or out-of-band communication to track workload interactions.
- Limited Visibility: Focusing on identities such as service accounts or secrets rather than the source and destination workload, server, service, etc.
- Lack of Transparency: Failing to identify new workloads as they come online, especially in dynamic environments.
- Lack of Actionable Insights: Struggling to prioritize which workloads are the most active and require attention first.
- Delayed Action: Discovering issues related to new servers and workloads only after they’ve become a problem, rather than proactively securing access.
That’s why we built Aembit Edge Discovery. This new capability, powered by our intelligent Aembit Edge component, provides a transparent, dynamic, and actionable way to bring your workloads under management.
How Aembit Edge Discovery Transforms Your Workload Security
Transparent and No-Code: The Aembit Edge is a lightweight agent deployed alongside your workloads, whether they’re running on virtual machines, bare metal servers, or even in containerized environments. It operates transparently, meaning there’s no need for your developers to alter their application code for discovery. Simply integrate Edge via your existing deployment automation tools, and it begins mapping access relationships seamlessly.
Dynamic and Continuous: Your infrastructure is constantly evolving, and so should your security. With Aembit Edge running, our platform continuously and proactively identifies new workloads and their access relationships as they come online. This dynamic approach ensures that no asset goes unnoticed, giving you a real-time, accurate picture of your workload landscape. This enhanced visibility is crucial for understanding your attack surface and identifying potential security risks before they can be exploited.
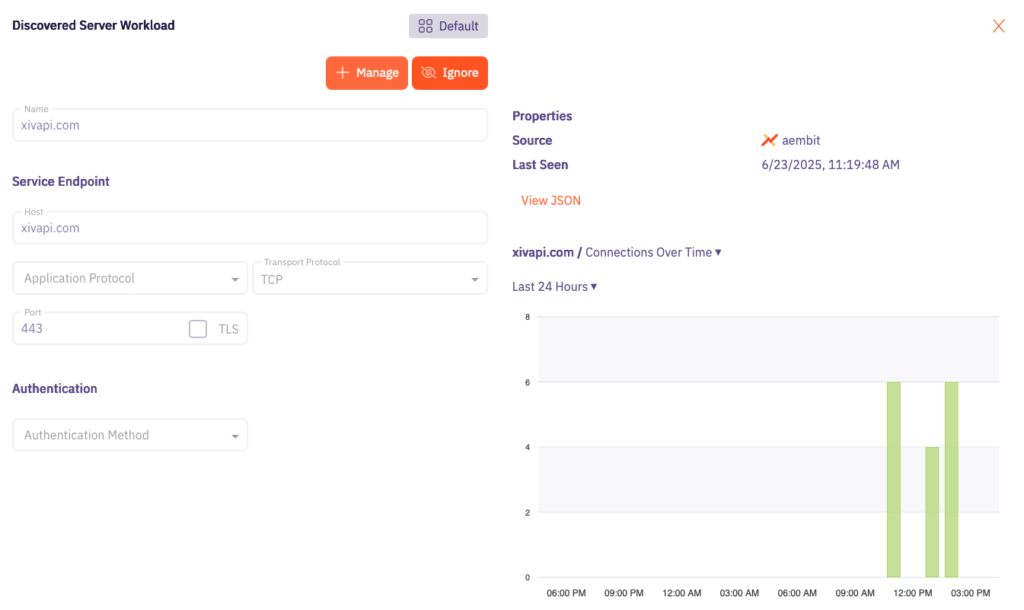
Actionable Insights for Policy Enforcement and Scaled Deployments: Discovery isn’t just about seeing. It’s about doing. Once a workload is identified by Aembit Edge, bringing it under the governance of the Aembit Workload IAM Platform is straightforward. Our intuitive interface allows you to quickly:
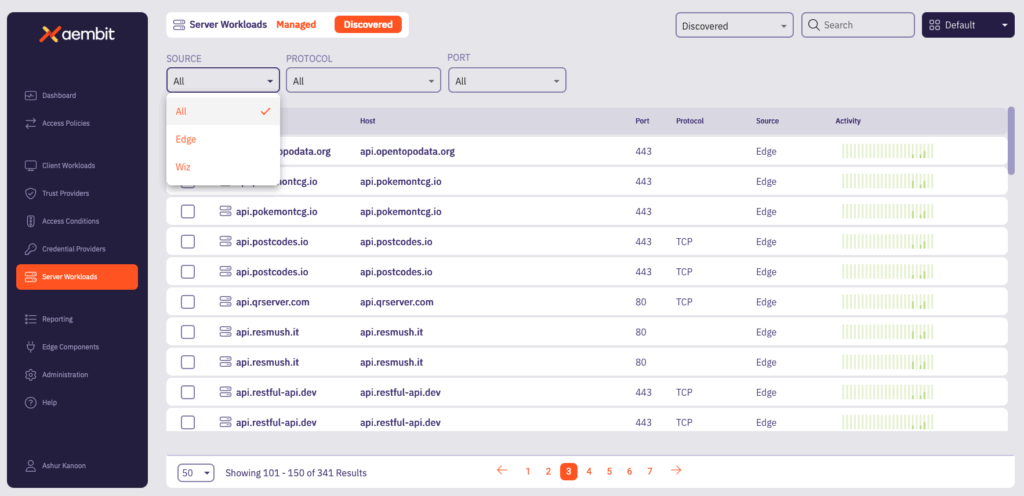
- Identify Client and Server Workloads: Clearly see who is accessing what, down to the protocol and port, and where those connections are happening. This distinction is vital for defining precise access policies.
- Understand Access Patterns: Gain a richer understanding of your workload activity than typical NHI discovery. The relationship between services, network loads, connection volumes, and more, allows you to prioritize higher risk workloads for better security and application performance.
- Streamline Policy Creation: Use the discovered information as the building blocks to define granular, identity-centric access policies.
Imagine moving from passively monitoring traffic to actively securing access with a few clicks.
Aembit Edge Discovery makes this possible by providing the foundational intelligence for your Workload IAM strategy. Furthermore, by automatically discovering client and server workloads, Aembit Edge Discovery significantly reduces the manual effort involved in scaling your deployments.
As you add new services or expand your infrastructure, the Edge agent instantly identifies these new entities, allowing you to rapidly extend your security policies without the need for cumbersome manual configuration.
Build With Confidence, Stay Secure by Design
Aembit Edge Discovery is a testament to our commitment to simplifying workload identity and access management. By automating the discovery process, we empower your security and DevOps teams to reduce operational overhead, accelerate your transition to secretless and identity-based access, and ultimately, build and deploy applications with greater confidence.
We invite you to explore Aembit Edge Discovery and experience the power of seamless workload visibility and control. Our ‘Starter Tier’ includes discovery and it’s free. To sign up, visit https://aembit.io/try-aembit
Learn more about how Aembit is redefining workload identity and access management by visiting our documentation here and here.